A real-time blackhole list (RBL) is a list of IP addresses that have been marked as sources of spam or other malicious content. Various organizations that monitor network traffic for such content keep the list regularly updated.
This article explains what the RBL is, its types, and its usage.
What Is Real-time Blackhole List (RBL)?
RBL is a DNS-based list of IP addresses or domain names that have been flagged for sending spam or engaging in malicious activity. Originally developed in the 1990s, RBLs were created to help email administrators block messages from known spam sources.
RBLs work by integrating with mail transfer agents (MTAs) like Postfix, Exim, or Sendmail. When a server receives a message, it performs a DNS query to one or more RBLs. If the sender's IP appears on a list, the message can be rejected outright or marked as suspicious.
The key advantage of RBLs lies in their efficiency and real-time functionality. Since lookups are done via DNS, they impose minimal delay, even under high traffic.
Most RBLs are curated by independent organizations, ISPs, or spam-fighting communities. Listings may be automatic, based on spam traps or heuristics, or manual, based on complaints.
Note: RBLs are not legally binding or universally consistent. One list may block an IP that others allow. That is why knowing how each RBL operates is important when troubleshooting email delivery issues.
Why Is RBL Important?
The increasing sophistication of spam and phishing attacks makes traditional filters less effective on their own. RBLs provide a proactive line of defense by preemptively blocking known sources of abuse before they reach the inbox.
The importance of RBL lies in:
- Spam reduction. RBLs block millions of unwanted messages before they even reach user-level filters.
- Server protection. RBL prevents your server from wasting resources processing spam messages or malicious payloads.
- Reputation management. Keeps your mail server's sending reputation intact by avoiding spam traps and complaint loops.
- Compliance. Many organizations rely on RBLs to meet email security standards or data protection regulations.
- Ease of integration. RBLs are widely supported and easy to configure within most MTAs.
Failing to use RBLs can leave your mail infrastructure vulnerable to open relay abuse, malware distribution, and loss of trust from recipient domains. For any organization relying on email communication, RBLs are an essential layer of email hygiene and delivery assurance.
Note: Under GDPR Article 32, many EU mail operators must document technical measures, including RBL usage, to prove they protect personal data against unauthorized access.
How Does Real-time Blackhole List Work?
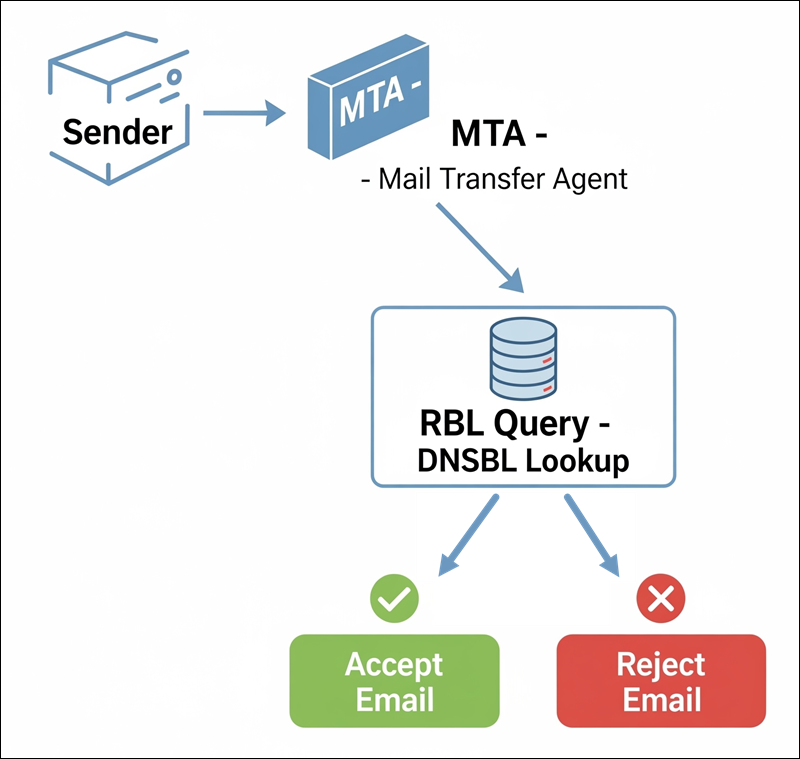
RBLs function through DNS queries. When an MTA receives an email, it extracts the sender's IP address and queries one or more RBLs in DNS format. If the IP is listed, the RBL returns a specific DNS record indicating a match.
The process works as follows:
1. The sender connects to your mail server via SMTP.
2. The server extracts the sender's IP address.
3. DNS lookup is performed in reverse format. For example, IP 192.0.2.1 becomes 1.2.0.192.rbl.example.com.
4. RBL server responds:
- 127.0.0.2: Listed
- NXDOMAIN: Not listed
5. The server acts: Reject, tag, or throttle, based on your policy.
This DNS-based mechanism allows for fast, efficient lookups and supports automation at scale. Some MTAs allow weighted scoring, which means that if an IP is listed on multiple RBLs, it gets a higher spam score.
The following diagram illustrates the process:
Note: Use RBLs responsibly. Overly aggressive blocking or using obscure lists may result in false positives. Always test and monitor their impact on email flow.
Different Types of Listings
Understanding the types of lists used in email filtering is essential for configuring accurate and effective policies. Refer to the list below for more details:
- Whitelist / Allow list. Contains IPs or domains explicitly trusted and bypasses filtering rules. Use for known partners or services (e.g., company SMTP relay).
- Blacklist / Block list. Lists known sources of spam or malicious activity. Typically results in rejection or message drop. The most common RBL use case.
- Grey list. Temporarily rejects messages from unknown senders. If the sender retries after a short delay, it is accepted. Useful against spambot attacks, which rarely retry.
- Yellow list. Less common. Marks senders with minor violations or suspicious behavior, but does not block outright. May contribute to a spam score.
- Dynamic list. Adds and removes entries automatically, in near real time, whenever threats are detected. Typical additions include IPs that repeatedly fail SMTP authentication or trigger abuse alerts on the server.
- Internal reputation scoring only. Some admins prefer internal scoring systems based on content, behavior, and connection patterns without using external RBLs.
Each of these list types serves a specific role and should be tuned according to the organization's risk tolerance and email usage patterns.
Well-known RBLs
There is a wide variety of RBL providers, but several well-known services stand out due to their reliability, scope, and reputation. These lists are commonly integrated into email filtering systems and used by major ISPs and enterprise mail servers.
The sections below list the best-known RBLs with their key characteristics.
Spamhaus
One of the most widely respected RBLs. Spamhaus maintains several lists:
- SBL (Spamhaus Block List) - IPs of known spam sources.
- XBL (Exploits Block List) - Malware-infected systems, open proxies.
- PBL (Policy Block List) - IPs that should not send email (e.g., dynamic ranges).
Spamhaus also provides DNS lookup zones and APIs for integration.
SORBS (Spam and Open Relay Blocking System)
Offers a broad database of spam-related activities, including:
- Open relays.
- Spam sent to honeypots.
- Dynamic IPs misconfigured as mail servers.
Sometimes criticized for being overly aggressive, but still widely used.
Barracuda
Barracuda's BRBL is used by its email security systems and is available publicly for non-commercial use. It lists IPs based on spam volume, failed authentication, and spam trap hits.
Delisting is available via a form after resolving the issue. It is less aggressive than some RBLs but can affect legitimate senders on shared IPs or misconfigured servers.
SpamCop
SpamCop is a dynamic RBL fed by user reports and spam traps. It reacts quickly to spam bursts and automatically removes IPs after 24-48 hours of clean behavior.
It is commonly used by mail servers for filtering. Delisting is automatic, although manual requests are possible if needed.
CBL (Composite Blocking List)
CBL lists IPs infected with malware, open proxies, or compromised software sending spam-like traffic. It feeds into other lists like Spamhaus XBL. Delisting is automated and available once the issue is resolved.
CBL focuses on:
- Infected machines (botnets).
- Proxy systems.
- Spam-sending malware.
Listing is automatic and updated frequently.
PSBL (Passive Spam Block List)
PSBL is a lightweight, community-maintained RBL that flags IPs based on passive spam traffic observation. It is less aggressive than others, and the delist process is easy via a simple web form after cleaning up the issue.
URIBL (URI Block List)
URIBL lists domains that appear in the body of spam emails, especially in links, not just sender IPs. It helps catch phishing and scam attempts. Delisting typically requires domain reputation cleanup and propagation time.
SURBL (Spam URI Realtime Blocklists)
Works similarly to URIBL but focuses on multiple spam-related domain sources, including comment spam and forum abuse. It is used alongside other filters to block emails linking to malicious or spammy sites. Delisting depends on the source list on which your domain appears.
Other RBLs
- Invaluement - Targets low-quality senders and graymail sources.
- UCEPROTECT - Controversial for blocklist logic, but still used.
- DNSBL.info - Aggregates data from multiple sources.
- Lashback - Tracks commercial senders who ignore unsubscribe requests.
- Mailspike - Uses spam-trap data and volume-based heuristics.
- SpamRATS - Lists bots, open relays, and compromised servers.
- NixSpam - German list based on honeypot data.
Use a combination of trusted RBLs to minimize false positives while ensuring effective spam blocking.
Common Reasons an IP Address/Domain May End up on RBL
Understanding the causes of getting listed helps prevent them. Common reasons include:
- Sending unsolicited bulk emails (spam). Even one campaign can trigger a listing.
- Hosting malware or phishing content. Detected URLs in the message body can get the domain listed.
- Open relays or SMTP misconfiguration. Allows third parties to send mail through your server.
- Compromised systems or accounts. Bots or malware using your system to send junk mail.
- Use of shared hosting or IPs. Other users on your server/network may get the whole IP range listed.
- High bounce or complaint rates. Indicates poor list hygiene.
- Sending to spam traps. Hidden addresses used only to catch spammers.
- Inconsistent email authentication. Missing or broken SPF, DKIM, or DMARC records.
- Unsubscribing violations. Not honoring unsubscribe requests can result in reports.
Preventive monitoring and best practices are critical in reducing the chance of being listed.
Consequences of an IP Address/Domain Ending up on RBL
Being listed on an RBL can seriously disrupt email operations and business communication. The consequences include:
- Email delivery failures. Messages bounce with 550-series errors (blocked or rejected).
- Delayed mail. Some servers defer suspicious emails, causing delays.
- Inbox placement issues. Mail might land in the spam folder instead of the inbox.
- Loss of trust. Customers may question your legitimacy if their providers block your emails.
- Damage to brand reputation. Associations with spam reduce credibility.
- Extra work for IT teams. Time spent diagnosing and fixing RBL-related issues.
- Blocked API or transactional messages. Affects services relying on confirmation or notification emails.
Some RBLs have cascading effects. Once one list includes you, others may follow. That is why fast detection and resolution are important.
How to Check If IP Address/Domain Is on RBL?
There are several methods for checking blacklist status. Proactive monitoring is the best way to detect issues before they escalate.
The sections below show how to detect if an IP address or domain is listed on RBL.
RBL Lookup Tools
There are online tools that aggregate results from multiple RBLs and provide quick status reports. Some of those tools are:
- MXToolbox - Clean UI and DNS tools integration.
- MultiRBL.valli.org - Checks over 100 RBLs.
- DNSBL.info - Free and widely used.
- Debouncer - Focuses on email reputation and spam traps.
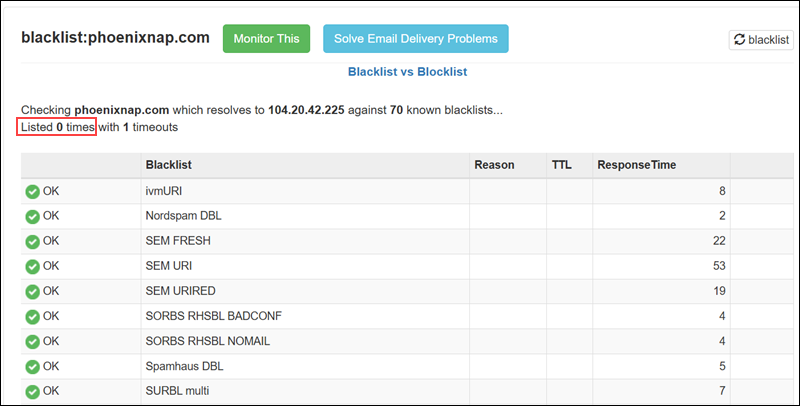
Just enter your IP or domain to check if it is listed. The example below shows MXToolBox:
Monitor Mail Server Connection Logs
Mail server logs provide direct evidence of RBL-based blocks and are one of the first places you should check when email delivery fails. When a recipient server rejects a connection due to an RBL, the response is typically logged with a 5xx SMTP error code and a message indicating the specific blacklist.
For example:
550 5.7.1 Service unavailable; Client host [203.0.113.5] blocked using zen.spamhaus.orgThese logs help pinpoint the exact RBL and rejection reason.
Email Deliverability Test
Email deliverability refers to how reliably your messages reach the recipient's inbox rather than ending up in the spam folder or getting rejected. Test deliverability to catch issues with authentication, reputation, and RBL listings before they affect users.
Deliverability refers to the ability of your email to reach the recipient's inbox. Use tools like:
- Mail-Tester
- GlockApps
- Postmark's Spam Check
They analyze headers, reputation, authentication, and RBL presence.
Document Specific Blocks
When your messages are rejected due to RBL listings, it is important to capture the exact response from the recipient server. Save error messages, SMTP codes, affected IPs/domains, and timestamps.
This documentation helps when contacting RBL maintainers or your email provider. It also provides a historical record to track repeat issues or identify trends.
Use Automated RBL Monitoring Service
Automated RBL monitoring tools check your IP and domain status across dozens of blacklists and alert you to new listings. These tools save time and help you act before users notice delivery failures.
Some automated RBL monitoring services are:
- HetrixTools
- RBLTracker
- DeBounce Monitoring
These services notify you immediately when your IP/domain appears on a blacklist. Most offer free and paid tiers.
How to Get IP Address/Domain Removed from RBL?
Being listed does not mean permanent damage, but you must act quickly and responsibly. Most RBLs allow delisting if you resolve the underlying issues and prove you are not a repeat offender.
Follow the steps below to ensure your domain is removed from RBL:
Step 1: Identify the Listing Source
Use tools like MXToolbox or MultiRBL to determine which RBLs have listed your IP or domain. This tells you where to focus your removal efforts, as each list has its own delisting process. For example, if you are listed on sbl.spamhaus.org, go to Spamhaus' removal portal and follow the on-screen steps.
When you complete the steps, submit your request and wait for the service to accept it.
Step 2: Investigate the Root Cause
To investigate the root cause of being listed, check the following:
- Mail server logs for unusual traffic or rejections.
- Spam reports or feedback loops (if available).
- Check if you are running open relays, outdated software, or compromised accounts, and resolve the issues.
If you are on a shared server, contact your hosting provider, as they may need to handle the removal.
Step 3: Fix the Issue
Before requesting removal, make sure to address the cause. Otherwise, you might end up on the list again.
Try the following to fix the issue:
- Enable outbound spam filtering.
- Require authentication for SMTP access.
- Configure SPF, DKIM, and DMARC properly.
- Update your mailing list hygiene (remove invalid emails, prune inactive users).
- Run malware scans on your systems.
If you do not fix the problem and end up on the list again, you risk escalating penalties for repeat offenders by some RBLs.
Step 4: Submit Delisting Request
To submit a delisting request, visit the RBL's website and:
- Fill out the delisting form on the website or email their abuse contact about your issue.
- Provide your IP/domain, a clear explanation of what went wrong, and what you did to fix it.
- Be polite and factual in your request and avoid accusations or frustrations.
Some RBLs automatically delist clean IPs after a time (e.g., after 24-72 hours).
Step 5: Monitor and Prevent Recurrence
After delisting, continue monitoring:
- Use automated tools to alert you about re-listing.
- Improve rate-limiting, authentication, and abuse detection on your infrastructure.
- Regularly review email practices and campaign metrics.
How to Avoid Getting IP Address/Domain on RBL?
Prevention is always better than remediation. Keep your IP reputation clean with good email hygiene, server configuration, and monitoring.
Below are some practical tips to stay off RBLs:
- Authenticate your email. Use SPF, DKIM, and DMARC to prove legitimacy.
- Use a reputable mail service. Use services like SendGrid, Mailgun, or Postmark to handle transactional or marketing mail.
- Avoid shared hosting for SMTP. Shared IPs are more vulnerable to collateral listing.
- Monitor outgoing traffic. Monitor your outgoing traffic and flag spikes, malformed messages, or connection floods.
- Clean your mailing list regularly. Remove inactive, bounced, or spam-trap addresses.
- Honor unsubscribe requests. Make sure to promptly execute unsubscribe requests and automate the process.
- Throttle suspicious senders. Limit the sending rate of internal users or applications that suddenly begin sending unusually high volumes of email to prevent potential blacklisting.
- Use double opt-in. Require subscribers to confirm their email address to prevent fake signups and reduce spam complaints.
- Filter outbound mail. Enable spam filtering on all outbound messages, even for authenticated or internal users, to catch compromised accounts.
- Monitor your sender reputation. Track your domain and IP health using tools like Google Postmaster Tools, Microsoft SNDS, and other reputation monitoring services.
Following these practices consistently can make a significant difference in protecting your IP/domain reputation.
Conclusion
This article explained Real-time Blackhole Lists (RBLs), critical components of email and network security infrastructure. While ending up on the list can feel like a crisis, the process for identifying and resolving the issue is manageable with the right tools and understanding.
Next, learn about Error 521 and what causes it, or check out our list of 16 best syslog servers for Linux and Windows.



