The shift from dial-up to broadband internet brought the challenge of managing individual user sessions over shared Ethernet infrastructures. The solution was the Point-to-Point Protocol over Ethernet (PPPoE), a protocol that replicates the session-based control of PPP within the framework of Ethernet architecture.
This article explains the Point-to-Point Protocol over Ethernet (PPPoE) and introduces its use cases.

What Is PPPoE?
Point-to-Point Protocol over Ethernet (PPPoE) is a network protocol that encapsulates Point-to-Point Protocol (PPP) frames within Ethernet frames. The encapsulation allows the transport of PPP sessions over Ethernet networks, enabling session management and user authentication in broadband access environments.
PPPoE combines the authentication, encryption, and compression functionalities of PPP with high-speed data transfer of Ethernet. It allows ISPs to manage individual customer connections on a shared network infrastructure.
How Does PPPoE Work?
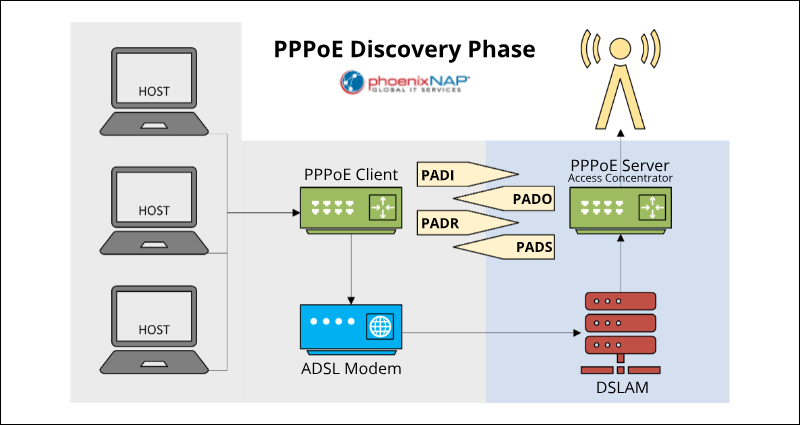
The operation of PPPoE involves two primary phases: the Discovery and the Session phase. The sessions are conducted between:
- The client side: The PPPoE client behind an ADSL modem.
- The carrier side: The PPPoE server (access concentrator) behind a digital subscriber line access multiplexer (DSLAM).
The Discovery phase determines the media access control (MAC) address of the access concentrator, which is typically an ISP's broadband remote access server (BRAS). The process consists of the following steps:
- The client initiates the discovery process by broadcasting a PPPoE Active Discovery Initiation (PADI) packet.
- The access concentrator responds with a PPPoE Active Discovery Offer (PADO) packet.
- The client selects an access concentrator and sends a PPPoE Active Discovery Request (PADR) packet.
- Finally, the access concentrator confirms the session with a PPPoE Active Discovery Session-Confirmation (PADS) packet.
The Session phase begins after the Discovery phase establishes a session, and the network is ready to encapsulate PPP frames within Ethernet frames. This phase has the following steps:
- Authentication. This step uses the Password Authentication Protocol (PAP) or the stronger Challenge Handshake Authentication Protocol (CHAP).
- Negotiation. The system performs IP address assignment and network configuration.
- Data transmission. The primary process of data exchange takes place.
- Termination. When necessary, PPPoE sessions are terminated by the client or the server, using a PPPoE Active Discovery Terminate (PADT) packet.
PPPoE vs. DHCP
PPPoE and Dynamic Host Configuration Protocol (DHCP) serve distinct purposes in network communication. While PPPoE focuses on establishing connections and performing authentication, DHCP handles IP address allocation and network configuration.
The table below summarizes the essential differences between the two protocols:
| PPPoE | DHCP | |
|---|---|---|
| Purpose | Creates secure, authenticated ISP internet connections (DSL, Ethernet, fiber); Enables residential broadband with user access control. | Assigns dynamic IPs and configures network settings in local networks; simplifies multi-device connection. |
| Scope | Operates between a client and an ISP. | Operates within a local network. |
| Authentication | Provides username/password authentication for security and access control. | Has no built-in access control. |
| IP assignment | Assigns static or dynamic IP addresses. | Leases IP addresses to devices for a specific period, allowing for efficient reuse of IP addresses. DHCP can also assign static IP addresses, based on MAC. |
| OSI model layers | Operates at Layer 2 (Data Link Layer) for discovery, session IDs, and Ethernet encapsulation, with aspects of Layer 3 (Network Layer), e.g., Network Control Protocols (NCPs). | Operates at Layer 7 (Application Layer), but relies on services from lower layers like Layer 4 (Transport Layer) for UDP, Layer 3 (Network Layer) for handling IP addresses, and Layer 2 (Data Link Layer) for MAC addressing. |
| Overhead | Higher due to session management and encapsulation. | Lower, without session management or encapsulation. |
| Complexity | Complex setup with authentication and session management. | Simpler, automatic IP assignment with minimal setup. |
PPPoE Use Cases
PPPoE is employed in the following broadband access scenarios:
- DSL connections. ISPs utilize PPPoE to authenticate and manage customer connections over DSL lines.
- Ethernet-based broadband. Some fiber-to-the-home (FTTH) deployments may use PPPoE for user authentication.
- Wireless ISP (WISP) networks. PPPoE can authenticate wireless subscribers who are connecting to a WISP access point.
- Public internet access points. In internet cafes or community networks, PPPoE helps providers authenticate users individually before they gain internet access. This action ensures secure and trackable connections for each user and allows the providers to charge by usage or time.
- Rate limiting and bandwidth control. PPPoE helps implement bandwidth limits and traffic management policies for individual subscribers.
How to Configure PPPoE?
PPPoE configuration consists of setting up client-side and server-side parameters, with the client-side configuration requiring the following actions:
- Entering a username and password provided by the ISP.
- Selecting a physical or logical network interface to send and receive the PPPoE discovery and session packets.
- Setting up the maximum transmission unit (MTU), i.e., the size of the largest protocol data unit (PDU) accepted in a single network layer transaction.
Note: The configuration process varies depending on the operating system or network device. Routers and modems typically provide a web-based interface for PPPoE setup.
On the server side, the actions include:
- Setting up the access concentrator.
- Integrating the authentication server (RADIUS).
- Managing the IP address pool.
- Configuring the BRAS.
PPPoE configuration is generally performed in the following order:
- Interface selection. Select the Ethernet interface on the client device or router.
- Authentication credentials. Enter the username and password provided by the ISP.
- Service name (optional). If required, specify the service name provided by the ISP.
- MTU configuration. Adjust the Maximum Transmission Unit (MTU) to accommodate PPP encapsulation. A value of 1492 bytes is standard.
- Authentication protocol selection. Choose PAP or CHAP authentication.
- IP address configuration. Obtain the IP address dynamically or statically, as provided by the ISP.
- Initiate connection. Start the PPPoE connection.
Note: The pppoeconf package allows for a guided PPPoE configuration on Linux-based systems. It scans the interfaces for an access concentrator and prompts the user for information (the interface, username, and password). Launch the wizard by typing sudo pppoeconf.
Conclusion
This article introduced PPPoE, its use cases, and configuration options. Despite newer solutions, PPPoE remains a relevant protocol for broadband access due to high compatibility and established infrastructure, particularly in DSL environments.
Next, learn about access control lists (ACLs) by reading What ACL in Networking Is and How to Implement It.