Docker has been the most popular container management engine on the market for a long time. However, as containerization became the norm in DevOps, competitors like Podman emerged as viable alternatives.
This article will compare two container management engines - Docker and Podman. It will also help you choose the right engine for your needs.
Note: Learn more about the differences between containers and VMs.
What Is Docker?
Docker is a popular platform for creating, deploying, and managing containers. Docker containers allow developers to apply a system-agnostic approach to software deployment. Since Docker runs the same containers on any operating system, containerized applications are cross-platform.
What Is Podman?
Podman is an open-source, daemonless, rootless container engine developed by RedHat and designed as an alternative to Docker. The modular design allows Podman to use individual system components only when needed. Its rootless approach to container management allows containers to be run by non-root users.
Podman vs. Docker: Comparison
In the following section, the article will go in-depth into the similarities and differences between Podman and Docker.
| Docker | Podman | |
|---|---|---|
| Daemon | Uses the Docker daemon. | Daemonless architecture. |
| Root | Runs containers as root-only. | Runs containers as root and as non-root. |
| Images | Can build container images. | Uses Buildah to build container images. |
| Architecture | Client-server. | Fork-exec. |
| All-in-one platform | Yes. | No. |
| Docker-swarm | Supported. | Not supported. |
| Docker-compose | Supported. | Supported. |
| SELinux support | Via a module. | Native. |
| Firewall interaction | Overrides firewall rules. | Does not override the firewall. |
| Runs natively on | Linux, macOS, and Windows. | Linux, macOS, and Windows (with WSL). |
Note: If you need Podman installed, refer to our installation guides on How to Install Podman on macOS and How to Install Podman on Ubuntu.
Architecture
Docker utilizes client-server architecture. The Docker daemon is a persistent background process that manages containers and maintains communication between the client and the server. The docker version command output shows separate sections for the client and the server versions:
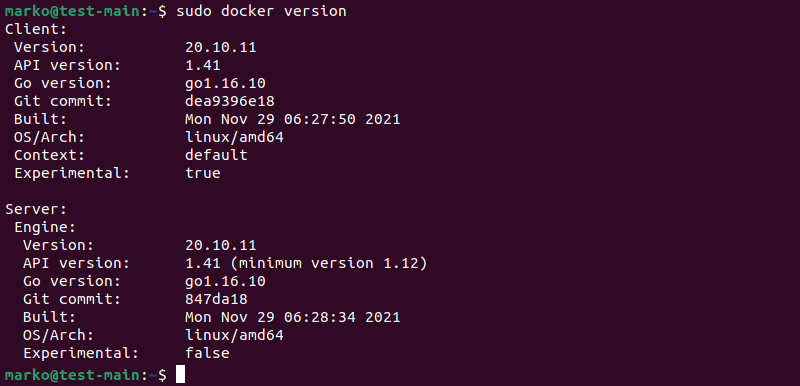
Another noteworthy feature of Docker is its all-in-one approach to container management. Docker provides all the necessary components for creating and running containers through its core application and integrated tools.
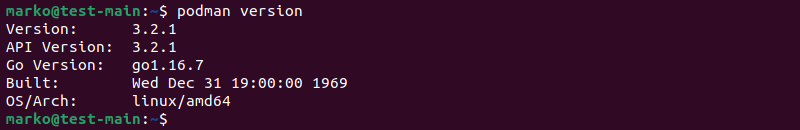
Podman manages containers using the fork-exec model. Since Podman is a process and does not use the client-server paradigm, it does not require a daemon to run. Podman containers are child processes of the primary Podman process. Using the podman version command shows that Podman lists only one version number:
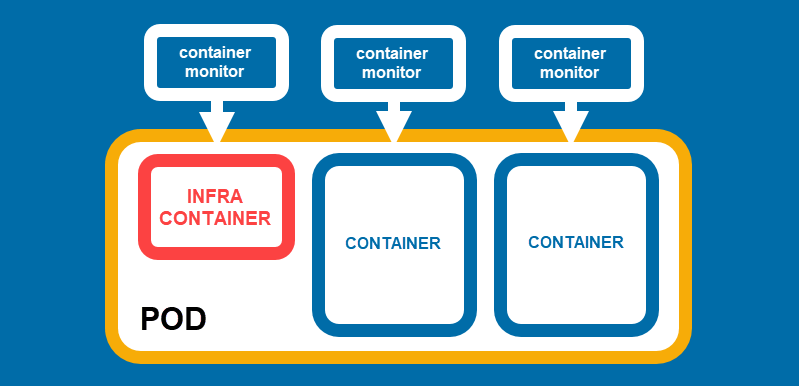
The central unit of Podman architecture is a container. However, Podman also introduces the pod concept. Like Kubernetes pods, Podman pods are groups of one or more containers that share the same system resources. The pod comprises the main container and sidecar (infra) containers supporting it.
Unlike Docker, which attempts to provide a single solution to containerization, Podman has been designed to run containers. Users perform the rest of the container management operations by extending Podman's functionality with additional tools such as:
- Buildah for image creation.
- Skopeo for image distribution and image repository manipulation.
- Nomad for scheduling and orchestration.
Note: Find out how Nomad compares to Kubernetes.
Ease of Use
Docker features a comprehensive set of intuitive commands. With Docker, developers can easily create, deploy, and manage containerized applications.
Podman was built to replace Docker in a software development workflow seamlessly, so its commands are mostly the same as Docker's. For example, the docker pull command becomes podman pull:
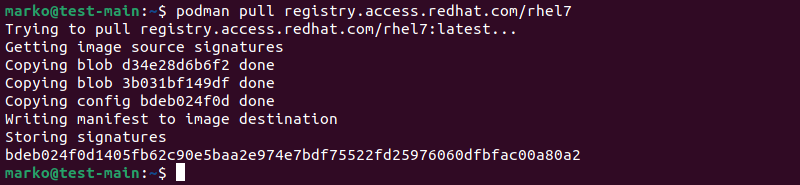
Aside from Podman inheriting the ease of use of Docker, the similarity between the two tools also means that the migration from Docker to Podman requires little effort.
Daemon Usage and Root Privileges
Docker features a background daemon process called dockerd. The daemon receives commands via Docker CLI and handles all the container management operations. The Docker's architecture requires the daemon to run as the root user, so the users need root privileges to interact with it.
Podman does not feature a central daemon process. Instead, Podman commands run as separate processes that do not require superuser privileges.
Rootless Execution
Users who are not in the docker UNIX group must run Docker commands using the sudo command. Running Docker in rootless mode is possible but requires installing additional packages and specific storage drivers.
Podman is rootless by design. Thanks to its modular architecture, granting different privileges to different users is possible.
Building Images
Docker uses the docker build command to build container images from a Dockerfile and a build context. The build context is a set of files specified in the Dockerfile used in container creation.
Podman features the podman build command that uses a syntax similar to docker build.
However, Podman performs the building process using Buildah, another open-source tool. When podman build is executed, the buildah bud (build-using-dockerfile) command is called to emulate the docker build command.
External Support
Both Docker and Podman can expand functionality with external tools. The sections below present some of those tools and compare how Docker and Podman interact with them.
Docker Swarm
Docker Swarm is a container orchestration platform for managing Docker containers. It enables developers to run a cluster of Docker nodes and deploy a scalable application without other dependencies required.
Podman does not support Docker Swarm. However, Podman users can use Nomad, which comes with a Podman driver.
Note: To read more about Docker Swarm and compare it to Kubernetes, read Docker Swarm vs. Kubernetes.
Docker Compose
Docker Compose is Docker's tool for managing multi-container application environments. It automates container initiation and management and streamlines the software development life cycle (SDLC).
Previous versions of Podman did not have a way to simulate the Docker daemon necessary for Docker Compose to work, so they used less user-friendly alternatives like Podman Compose. However, as of version 3.0, Podman supports Docker Compose via podman.socket, a UNIX socket that replaces the Docker daemon.
SELinux
SELinux is a framework that provides an extra layer of security to Linux systems, built as an extension of Access Control Lists (ACLs). Docker has an SELinux module, but Podman's implementation is native and more user-friendly. On an SELinux-enabled OS, each container run by Podman has a SELinux label that prevents external processes from accessing the container's files.
Security
Docker is a secure tool, although some aspects of its design need attention from a security standpoint. Take the following into consideration when using Docker:
- Running containers in privileged mode is not recommended. Docker is secure only when the containers are run in the default, non-privileged mode.
- Docker can interfere with firewall rules. Iptables rules inserted by Docker are placed before firewall rules, effectively ignoring the firewall. Unless properly addressed, this behavior can cause serious security issues.
Note: Docker's security can be increased further by enabling AppArmor, SELinux, and GRSEC, and applying security best practices.
Podman's fork-exec architecture makes it a more secure solution than Docker. Below are some of the ways in which Podman provides more security:
- More in-depth audit logging. Podman's fork-exec model lets the system record the user modifying the system files correctly. However, the client-server approach that Docker uses does not provide this feature.
- Rootless containers. Assigning specific privileges to specific users gives administrators better access control for critical server components.
- No interference with firewall rules. Podman enables container networking by creating an internal network whose rules cannot override external firewall rules.
Note: OCI containers hosted on Bare Metal Cloud offer better performance and efficiency than those hosted on cloud VMs.
Podman vs. Docker: How to Choose
Choose Docker if you:
- Prefer a well-documented tool. Docker's main advantage over Podman is its widespread use. A large amount of Docker-related support means that searching the internet can resolve many potential issues.
- Require container orchestration support. Docker Swarm support is another benefit of Docker. Users who want to orchestrate Podman containers must resort to less feature-rich alternatives than Docker Swarm or dive into Kubernetes. While popular, Kubernetes has a steep learning curve and may be too complex for simple projects.
Choose Podman if you:
- Emphasize security. Podman's architecture is inherently more secure than Docker's.
- Plan to move to Kubernetes down the road. Podman introduces the pod concept, which makes it a good starting point for Kubernetes.
- Use systemd. One of the main benefits of Podman compared to Docker is that Podman fully integrates with systemd by default. This feature enables Podman to run systemd within the container out of the box.
Podman vs. Docker: FAQ
Since Podman and Docker have similar functionality and cater to the same use cases, deciding which one to use can be problematic. Below, you can find some of the most commonly asked questions concerning the comparison between Podman and Docker.
Can Podman Replace Docker?
Podman alone does not fully match Docker in features. However, using Podman alongside its companion tools (Buildah, Skopeo, Nomad, etc.) can fully replace Docker.
Is Podman More Secure than Docker?
Yes, Podman is rootless by design, which makes it a more secure solution. Its daemonless design removes the single point of failure created by Docker's central daemon.
Is Podman Compatible with Docker?
Since both Docker and Podman are OCI-compliant, they can be used side-by-side. For example, Docker's robustness can be employed on development machines, while dev, int, and prod environments can benefit from Podman's increased security.
Can Docker Images Be Used with Podman?
Yes, Podman can run containers with images created in Docker and vice versa. The two platforms support the same image format.
Conclusion
After reading this article, you should know more about the similarities and differences between Docker and Podman.
To improve your work with containers, read more about monitoring Docker containers.
For more containerization platforms, check out our list of 10 Docker alternatives.