Docker is a popular containerization solution that offers robust security features, speeds up app deployment, and facilitates software development. However, Docker is not always the best option, especially for use cases that do not require all of the platform's features.
This article will present 10 Docker alternatives to help you replace Docker in your workflows.
Docker Alternatives
The following list of Docker alternatives contains solutions that either completely replace Docker's functionality (e.g., Podman) or provide a replacement for specific aspects of the containerization process (e.g., the runC container runtime). The article divides the tools into four categories:
- Image builders. Image-building utilities help create OCI-compliant container images.
- Container managers. In a broader sense, container management can be used to describe most of the actions related to building and running containers. However, the specific purpose of container managers is to help users manage container instances.
- Container runtimes. Tools that deal with the process of running a container. The process includes namespace and cgroup configuration, preparing a container mount point, resource allocation, etc.
- Container engines. Also known as high-level container runtimes, container engines control all the management aspects of the containerization process.
Read the sections below to learn more about each tool.
1. Buildah
Type: Image builder
Buildah is RedHat's open-source image-building tool that allows users to create OCI-compliant images without installing a daemon or a container runtime. The daemonless nature of Buildah makes it possible to build images as a non-root user.
Although you can use Dockerfiles to create images with Buildah, they are not required for Buildah to function. Instead, the tool can build images using existing images or entirely from scratch.
Furthermore, Buildah allows scripting and shell operations to be performed during the building process. For example, the following command assigns the new container name to the container shell variable.
container=$(buildah from fedora)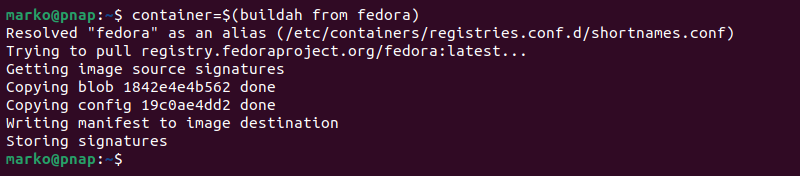
You can use Buildah as a standalone application or with tools such as Podman and Skopeo.
2. BuildKit
Type: Image builder
BuildKit is an image builder created by Moby, a Docker framework for assembling specialized container systems. Although its primary purpose is to replace the legacy builder inside Docker, BuildKit also works as a standalone tool.
A distinguishing feature of BuildKit is parallel build processing. Docker can only build one image layer at a time, while BuildKit can work on multiple layers simultaneously, significantly improving the build speed.
BuildKit also improves layer caching and allows incremental builds. With its pluggable architecture, the tool often helps streamline CI pipelines by building images and deploying them to a Kubernetes cluster.
Note: Like Buildah, BuildKit does not require root privileges. However, unlike Buildah, it runs using a daemon.
3. Kaniko
Type: Image builder
Kaniko is a Google container tool that can build a Dockerfile-based image inside a Kubernetes cluster or another environment in which the Docker daemon is unavailable. Since it does not require a Docker daemon, Kaniko can run in rootless mode and execute each Dockerfile command in userspace.
Users can deploy Kaniko:
- In a Kubernetes cluster.
- In Docker, e.g., inside a Docker container.
- With Google Cloud Build.
- With gVisor, an application kernel for containers.
Kaniko runs as a container based on the official image. The container uses a Dockerfile and build context arguments to create and push an image to the specified registry.
Note: Hosting OCI containers on Bare Metal Cloud is a way to achieve better performance and flexibility compared to standard VM-based solutions.
4. LXD
Type: Container manager
LXD is a Linux container and virtual machine manager developed by Canonical. It offers a simple CLI tool called lxc to deploy and manage Linux OS container instances. With lxc, users can specify the Linux distribution to run and provide configuration parameters, like in the example below:
lxc launch images:ubuntu/22.04 test-container --config limits.cpu=1 --config limits.memory=192MiB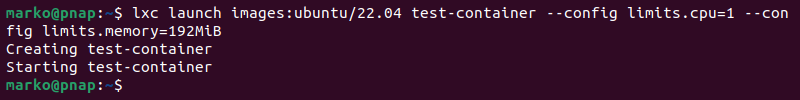
LXD uses Core API, a secure solution that allows the creation of unprivileged containers. It provides a way to restrict resource usage and enables secure authentication. Furthermore, LXD supports restoring instances with snapshots, transferring images between hosts, and profile-based configurations.
5. Vagrant
Type: Container manager
The idea behind HashiCorp's Vagrant is to provide a consistent workflow for development projects that span across different operating systems. While Docker is efficient for this use case, Vagrant supports more operating systems (notably, BSD).
With Vagrant, users create a virtual environment to replicate on various operating systems and VMs. This feature facilitates collaboration between team members working on the same software development project and ensures that the code runs consistently.
Note: Start working with Vagrant by learning the basics in our Vagrant Beginner Tutorial.
6. Portainer
Type: Container manager
Portainer is a cross-platform web UI tool that helps manage multiple container environments. Aside from Docker, Portainer supports orchestration platforms like Azure ACI, Kubernetes and Docker Swarm.
Thanks to its server-agent architecture, integrating Portainer in a Kubernetes cluster is straightforward. The diagram below illustrates this integration, with the server instance residing on the Kubernetes master node and an agent instance deployed on each cluster node.
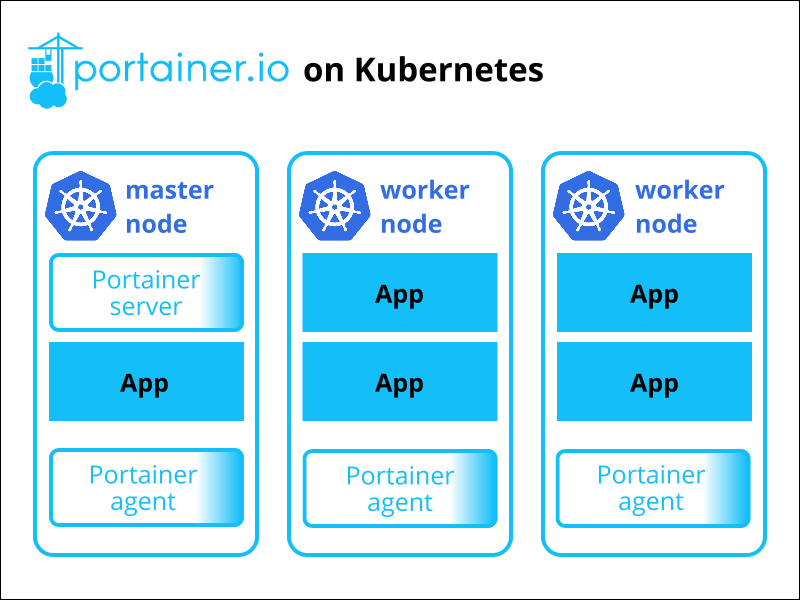
Portainer aims to be a beginner-friendly solution and simplifies container orchestration by providing a GUI. Inside a cluster, Portainer allows pre-configuration of cluster settings, facilitates user account creation and RBAC, and allows defining cluster policies.
7. containerd
Type: Container runtime
containerD is a runtime tool that manages image transfer and storage and creates OCI containers. It is integrated into the Docker platform but can also act as a standalone solution for container creation in Kubernetes. To directly communicate with the Kubernetes orchestrator, containerD needs the CRI compatibility plugin.
8. runC
Type: Container runtime
Similar to containerD, runC is a Docker CLI tool. It is a universal, portable container runtime written in the Go language that can work independently from Docker.
runC follows the OCI specification to spawn and run containers. It is considered a standard for low-level container runtimes thanks to its support for all major Linux security features, native support for many hardware architectures, and a formally defined configuration format.
Note: Learn more about containerd and runC and how they compare to Docker and CRI-O in Docker vs. containerd vs. CRI-O: An In-Depth Comparison.
9. Podman
Type: Container engine
Podman is a daemonless container engine for OCI container management on Linux. It is designed as a full-fledged Docker replacement but has some fundamental differences.
Below are the three main Podman design features that differentiate it from Docker.
- Daemonless. Docker uses a daemon process to establish communication between the server and client sides of the application, while Podman features a single process with child processes.
- Rootless. Creating a container in Podman does not require root privileges.
- Container-focused. Podman only deals with running containers and uses other tools to perform image building (Buildah), image distribution (Skopeo), and similar container management actions.
Podman also introduces the concept of a pod, a group of containers that share system resources. Each pod contains an infra container, which keeps the pod alive, and regular containers. The diagram below illustrates a Podman pod.
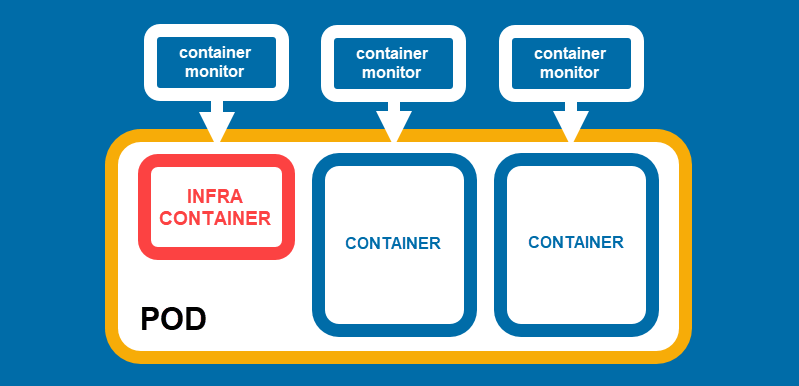
Thanks to its rootless nature, Podman is more secure than Docker. However, Docker is still a better solution for those who are looking for an all-in-one container management solution.
Note: For an in-depth comparison between Podman and Docker, read Podman vs. Docker: Everything You Need to Know.
10. rkt
Type: Container engine
rkt is an application container engine formerly known as CoreOS Rocket. Similar to Podman, its central execution unit is a pod, a concept that allows resource and environment sharing.
Pods in rkt run as Unix processes without a daemon controlling them. rkt supports all crucial Linux security features and integrates well with init systems such as systemd and upstart.
Conclusion
This article presented 10 tools that can replace Docker in various container management aspects. After reading it, you should have a shortlist of tools that could replace Docker in your development and app management workflows.
Next, read about 12 Docker container monitoring tools to improve your Docker monitoring.