Homomorphic encryption (HE) is a cryptographic method that allows computations on encrypted data without exposing its contents. It is essential in modern cybersecurity because it enables data processing without revealing sensitive information.
Standard encryption protects data at rest and in transit. However, it requires decoding data for processing, which exposes it to security risks. HE avoids this issue by allowing operations on encrypted data.
This guide explores homomorphic encryption, its key uses, limitations, and the best scenarios for adopting it.
What Is Homomorphic Encryption?
Homomorphic encryption is a type of encryption that allows calculations on encrypted data without decryption.
Consider a scheme such as Paillier, which supports homomorphic addition. It allows adding ciphertexts to get an encrypted sum.
For example, if there are two salaries:
- Salary A: $50,000
- Salary B: $60,000
Each salary is encrypted:
- CA = Encrypt(50000) = 8723948723984723
- CB = Encrypt(60000) = 3298472398472398
Adding these ciphertexts creates another encrypted value. Decrypting the result gives the same sum as adding the original numbers:
- Decrypt(CA + CB) = 50000 + 60000 = 110000
This process ensures private data remains protected during processing.
Note: The example values are for demonstration purposes only. Actual encrypted data is longer and more complex.
Traditional encryption needs to decode the data before processing, which exposes it to potential threats. In contrast, HE keeps data hidden during the operation.
Types of Homomorphic Encryption
There are three main types of homomorphic encryption. They all use variations of public key cryptography to encode and decode data. The main difference between these types lies in the type and number of operations they support.
Note: Public key cryptography relies on proper key management. See our list of best encryption key management practices to ensure your keys stay safe.
Partially Homomorphic Encryption (PHE)
PHE supports a single operation:
- Addition (Paillier).
- Multiplication (RSA or EIGamal).
The scheme is simple and useful for basic secure computations.
Somewhat Homomorphic Encryption (SHE)
SHE supports addition and multiplication, but only for a limited number of operations. Each operation adds noise, making decryption impossible after many calculations.
The scheme was used in early versions of privacy computations and in cases where only a few operations are needed.
Fully Homomorphic Encryption (FHE)
FHE supports unlimited additions and multiplications. The scheme removes noise buildup and allows calculations as often as needed.
This scheme is perfect for cloud computing and AI applications where encrypted data must be processed securely.
Note: Craig Gentry developed the first fully homomorphic encryption (FHE) scheme in 2009, allowing unlimited computations on encrypted data. His bootstrapping method made FHE practical and advanced secure computing.
Benefits of Homomorphic Encryption
Homomorphic encryption improves data privacy and security, so it is well-suited for privacy-sensitive applications.
The main advantages are:
- Compliance and data protection. Homomorphic encryption helps organizations meet data privacy laws, such as GDPR, HIPAA, or CCPA. It keeps data encrypted and shows decrypted results to users with the decryption key.
- Improved data privacy. Data stays hidden, reducing unauthorized access risks.
- Secure outsourcing and collaboration. Third-party providers cannot access unencrypted plaintext data, preventing data leaks and ensuring confidentiality.
- Decreased breaches. Data remains encrypted at all times. If a system is compromised, attackers cannot access the meaningful raw data.
- Maintained data integrity. Calculations performed on encrypted data are accurate. The results are verifiable when decrypted, and the original data remains unaltered.
Note: See also our in-depth guide on the best cybersecurity practices.
Homomorphic Encryption Use Cases
Homomorphic encryption is an area of cryptography with numerous uses. Below are a few example use cases in different industries.
Data Analysis
Organizations with personal or confidential data can perform analysis without compromising privacy. Homomorphic encryption allows different kinds of analysts to perform various operations on encrypted datasets.
Whether the operations are related to statistics, machine learning, or data mining, the process maintains privacy while giving valuable insights.
Cloud Computing
Users can encrypt data before storing it in the cloud, keeping it private. Cloud servers and the provider are not given access to the data, but they can still perform computations.
Homomorphic encryption allows private data processing in the cloud and guarantees that it remains hidden from the provider.
Note: Check out our tips on how to choose a cloud provider.
Healthcare
Healthcare data contains patient details that must be protected under regulations. HIPAA violation fines and penalties are costly, but sharing medical data is often required for additional analysis and research.
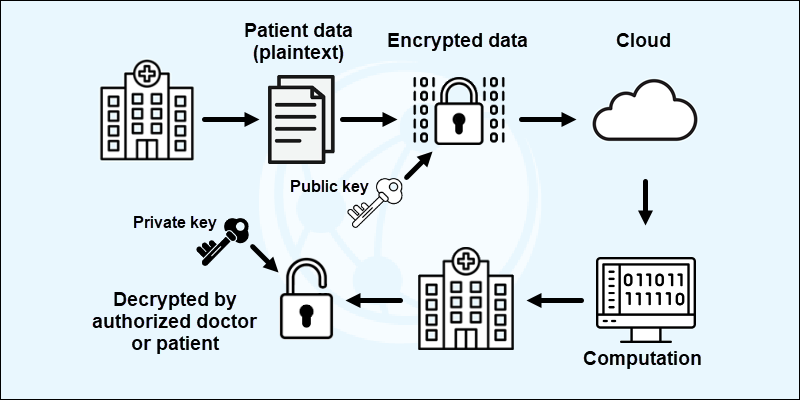
Homomorphic encryption can hide patient data and enable critical research, analysis, and innovation in the healthcare field. It ensures compliance with privacy regulations by not revealing personal or medical details during the analysis.
Finances
Financial services and institutions handle highly sensitive data. This data includes bank account details, transaction logs, and credit scores.
Banks and other financial businesses can use homomorphic encryption to perform calculations on encrypted data. It enables risk assessment or fraud detection without compromising a customer's privacy.
Voting
Online voting systems require privacy and data integrity to guarantee the election process is valid. Homomorphic encryption encrypts voting details while allowing the authorities to tally the votes accurately.
By not decrypting the underlying data, the process ensures election confidentiality. It helps eliminate voting bias or result tampering.
Third-Party Processing
Organizations often offload heavy computational tasks to third-party providers. However, they don't want to expose private data, such as proprietary algorithms or details.
With HE, organizations have a secure way to outsource data to third-party servers. The computation is done on encrypted data, which ensures that anything private remains confidential.
Limitations of Homomorphic Encryption
Although there are many privacy and cybersecurity benefits, homomorphic encryption has limitations. The main challenges include:
- Overhead. HE requires more computing power than traditional encryption. Its high resource demands make it impractical for large-scale or real-time technologies.
- Efficiency and speed. Encrypted calculations take much longer than standard operations. The lower speeds make HE impractical for enterprise uses.
- Capabilities. HE encryption works well for basic math. However, complex operations like sorting and conditional logic are hard to implement.
- Security. HE is not immune to cryptographic attacks. Cryptanalysis and quantum computers may weaken these schemes. Emerging threats require continuous updates and innovations, as with all cryptographic techniques.
Current research aims to improve HE's efficiency and expand its uses. As these improvements continue, HE will play a more significant role in secure cloud computing.
Note: Read how homomorphic encryption helps with privacy in AI.
When to Use Homomorphic Encryption
Homomorphic encryption works best in situations where data privacy and computation are essential. Here are some cases where using this encryption makes sense:
- Third-party processing. Outsourcing computations on confidential data to cloud providers is possible due to HE. Companies can use data analytics through a cloud service without risking exposure.
- Data confidentiality and compliance. Organizations that work with personal, financial, or medical data must maintain legal compliance. These industries access the data for various reasons, and HE can ensure privacy in these cases.
Avoid using HE on large datasets, real-time data, or when simple encryption methods are sufficient.
Conclusion
This guide explained what homomorphic encryption is and how it works. It provided use cases, benefits, and drawbacks.
Next, read more about the best practices and challenges of cloud security and see how to create an effective cloud security strategy.