A Certificate Signing Request (CSR) is a cryptographic file generated on the server where you plan to install a certificate. It is the first step in setting up an SSL Certificate on your website.
The CSR contains information (such as the common name, organization, country, etc.) that the Certificate Authority (CA) uses to create the certificate. It also contains the public key that will be included in the certificate, and it is signed with the corresponding private key.
This guide will show you how to generate a Certificate Signing Request using OpenSSL.

Prerequisites
- A user account with root privileges.
- If you are working on a remote server, an established SSH connection to the server.
- OpenSSL installed on your system.
- A text editor to view your key.
Generate OpenSSL Certificate Signing Request
Creating a CSR is a simple process that includes running a few commands and editing the configuration on a Linux server. Follow the steps outlined below to create a CSR using OpenSSL.
Step 1: Check OpenSSL Version
The cryptographic algorithms used for generating keys and the supported protocols depend on the OpenSSL version. Knowing which OpenSSL version you have is especially important when troubleshooting possible issues.
The latest OpenSSL version at the time this article was written was 3.2.0. It supports Transport Layer Security (TLS) versions 1.0 to 1.3, while various cryptographic algorithms are deprecated due to security vulnerabilities.
Check your OpenSSL version by running the command below:
openssl version -a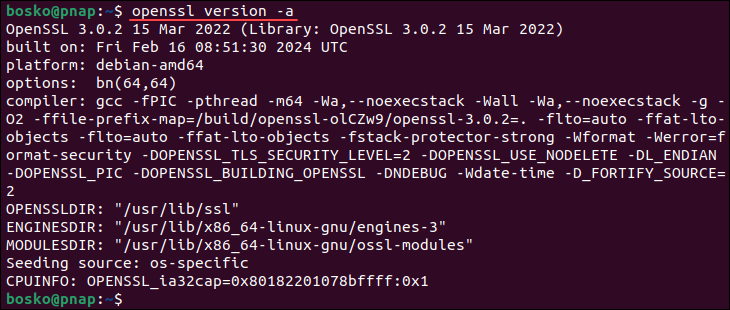
The -a flag displays complete version information, including the version number and version release date, the options built with the library, and the directory for storing certificates and private keys.
Step 2: Log Into Server
Open a terminal window and SSH into your remote server. Use the following syntax:
ssh [username]@[host_ip_address]Note: If you are working locally, you don't need an SSH connection. To launch a terminal window on most Linux systems, press Ctrl+Alt+T or Ctrl+Alt+F1.
Step 3: Create RSA Private Key and CSR
Issue a new private key each time you generate a CSR. Use the syntax below to generate a private key and the CSR:
openssl req -new -newkey rsa:2048 -nodes -keyout [your_domain].key -out your_domain.csrReplace [your_domain] with the actual domain for which you are generating a CSR.
In the above command:
openssl- activates the OpenSSL software.req- indicates that we want a CSR.-new -newkey- generates a new key.rsa:2048- generates a 2048-bit RSA mathematical key.-nodes- no DES, meaning do not encrypt the private key in a PKCS#12 file.-keyout- indicates the domain for which you are generating a key.- -out - specifies the name for saving the CSR file.
Note: Use 2048-bit key pairs. The 4096-bit key pairs are more secure, but they require a lot more server resources.
Step 4: Enter CSR Information
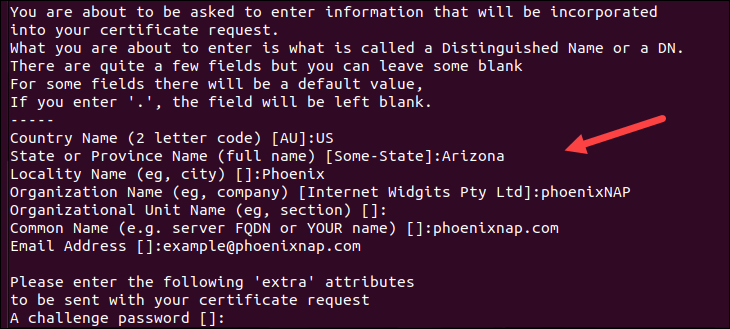
Your system should launch a text-based questionnaire for you to fill out.
Enter your information in the fields as follows:
- Country Name - a 2-letter country code (US for the United States).
- State - the state in which the domain owner is incorporated.
- Locality - the city in which the domain owner is incorporated.
- Organization name - the legal entity that owns the domain.
- Organizational unit name - the name of the department or group in your organization that deals with certificates.
- Common name - typically, the fully qualified domain name (FQDN), which users type in a web browser to navigate to your website.
- Email address - the webmaster's email address.
- Challenge password - an optional password for your key pair.
Please take into account that Organization Name and Unit Name must not contain the following characters:
< > ~ ! @ # $ % ^ * / \ ( ) ? . , &
For example:
Step 5: Locate Certificate Signing Request File
After you provide the details and the software finishes creating the CSR file, you should find it in your working directory.
You can also run the following command to find CSR files on your machine:
ls *.csr
The system should list all certificate signing requests. The one that matches the domain name you provided in Step 2 appended with the .csr extension is the one you need to look into.
Step 6: Verify CSR Information
After creating the CSR file, verify that the information is correct and that no modifications were made.
Use the following syntax to view the contents of the CSR file before submitting it to a CA:
openssl req -text -in [file_name].csr -noout -verifyThe -noout flag omits the output of the file, while the -verify flag checks the signature to ensure it has not been modified.
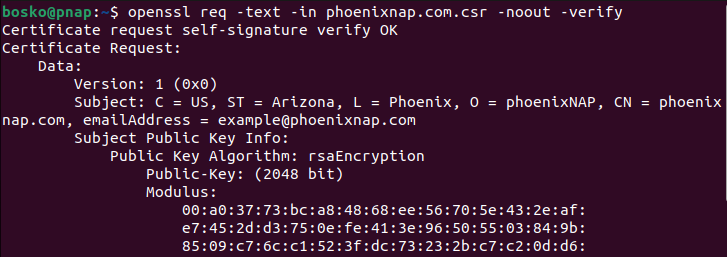
The output states whether the file was verified and shows the information you provided when you created the CSR file. If any information is incorrect, create a new CSR file and fix the errors.
Step 7: Submit CSR as Part of Your SSL Request
To complete the process and submit the CSR as part of your SSL request, open the .csr file in a text editor and copy the alphanumeric code.
Use the following syntax to open the file in nano:
sudo nano [file_name].csrYou can copy and paste the text into a submittal form to request your SSL certificate from a Certificate Authority. Make sure to copy the entire text. Some CAs may allow you to upload the .csr file you generated. Below is an example of a CSR:
There is no need to send the private key to the CA. Once you get your SSL certificate, the server's private key will be used to encrypt the communication.
How to Verify Certificate Information from CA
After receiving your certificate, it is a good idea to verify that the certificate information matches your private key. Verify the information using the openssl command. The syntax is:
openssl x509 -text -in [file_name].crt -nooutThe command outputs the contents of your certificate.
Additionally, use the following syntax to check the certificate's validity, its issuer, and whether it's been revoked (if CRL or OCSP information is available):
openssl verify [file_name].crtConclusion
This article showed how to generate an OpenSSL certificate signing request. SSL is a crucial protocol for securing traffic between a website and its visitors. It helps protect sensitive information online, such as credit card data.
Next, see how to fix Error 526 Invalid SSL certificate, or take a look at our ultimate guide for SSL certificate types.