OpenSSL is an open-source cryptographic library and SSL toolkit. The applications contained in the library help create a secure communication environment for computer networks. OpenSSL contains an implementation of SSL and TLS protocols, meaning that most servers and HTTPS websites use its resources.
In this tutorial, learn how to find the OpenSSL version on your system.

Prerequisites
- Access to a terminal window (Ctrl + Alt + T).
- OpenSSL installed on your system.
How to Check OpenSSL Version
The openssl version command allows you to determine the version your system is using. This information is useful to determine if a particular feature is available, verify whether a security threat affects your system, or perhaps report a bug. Follow the steps below to check your OpenSSL version:
1. Open the Terminal in Linux or the Command Prompt if you are using Windows.
2. Run the following command:
openssl version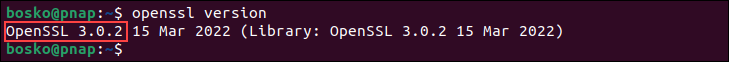
The output shows the OpenSSL version designation and the date of its initial release:
We can break down the version format to get valuable insight. Additionally, using flags helps structure the data. The sections below explain how to understand the version information in detail and how to use flags to format the data.
Understanding the OpenSSL Version Format
The version information format provides a lot of information. The position of the numbers represents the release type:
- Major Releases. You can recognize a major release if the first digit changes. This type of release can break compatibility with previous versions, for example, 2.0.0 vs. 3.0.0.
- Minor Releases. A minor release changes the second number of the version designation, e.g., 3.0.0 vs. 3.1.0. These releases are likely to contain new features; however, they should not break binary compatibility. You do not need to recompile applications to benefit from them.
- Patch Releases. A patch release changes the final number in the version, fe.g., 3.0.0 vs. 3.0.1. It only contains bug and security fixes, and the API and ABI remain compatible across patch releases.
OpenSSL Version Command: Flags
There are several flags that modify the openssl version command output.
The -help flag lets you see an overview of all valid options for the openssl version command:
openssl version -help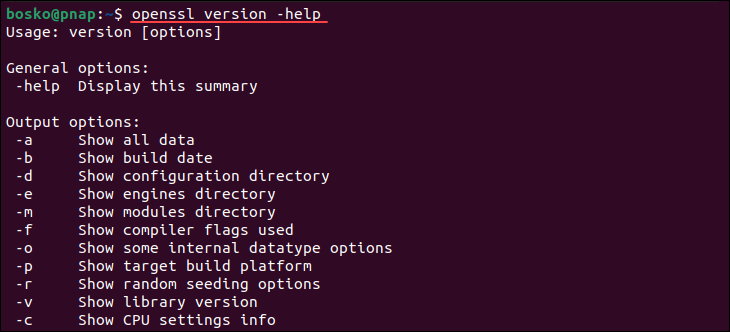
The output shows the options that allow you to narrow down your search. The option that provides the most comprehensive set of information is:
openssl version -aThe -a flag compiles all the information contained under the individual flags into a single output:
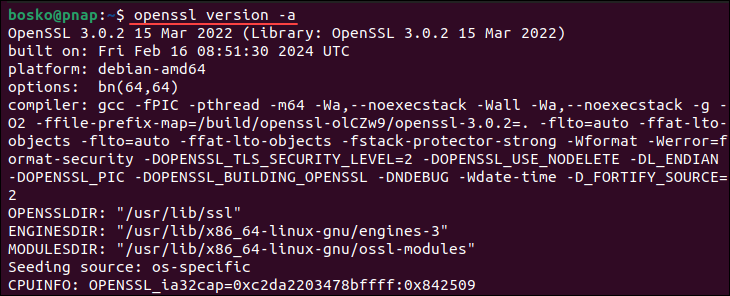
This option is convenient when troubleshooting or composing a bug report.
The OPENSSLDIR line tells you where OpenSSL looks for its configurations and certificates. You can print that specific line by specifying the -d flag:
openssl version -d
In the example above, the configuration files and certificates are located at /usr/lib/ssl.
If you specify the -c flag, the command provides CPU information that indicates which cryptographic operations or optimizations OpenSSL can take advantage of based on your CPU's capabilities. For example:
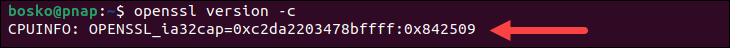
In the example above:
0xc2da2203478bffffrepresents a set of 64 bits, each corresponding to a specific CPU feature or capability.0x842509represents additional CPU features or optimizations specific to OpenSSL.
OpenSSL uses this information to detect certain CPU capabilities that can be used to optimize cryptographic operations.
OpenSSL Version: FAQ
This section reflects on some frequently asked questions about the OpenSSL version.
What Is the Latest OpenSSL Version?
At the time this article was written, the latest OpenSSL version available on the official website was 3.2.1. However, note that the version that ships with your OS may be older, which is the case with Ubuntu.
The default version that comes with Jammy Jellyfish is 3.0 since Ubuntu focuses more on stability rather than cutting-edge features, and 3.0 is the latest LTS (long-term release) version.
What Should I Do if my OpenSSL Version Is Outdated?
If your OpenSSL version is outdated, use your package manager to update it or download the latest version from the official website. You can check for updates in Ubuntu using the following command:
sudo apt install opensslThe command updates the OpenSSL package if a newer version is available in the repository. If there are no upgrades available, the output states 0 packages updated.
If you want the cutting-edge version on Linux, you must download and compile the source file since the repository only contains the stable version.
How Often Should OpenSSL Be Updated?
OpenSSL has long-term releases that receive support and fixes for the next five years. The LTS version at the time this article was written is OpenSSL 3.0, and it will be supported until 7 September 2026.
The frequency of updating your OpenSSL version depends on several factors:
- Security Updates. OpenSSL releases patches for security vulnerabilities as they are discovered. It is recommended that you install the patches when they are released to protect your system from potential exploits and security breaches.
- Feature Updates. OpenSSL usually introduces new features and improvements with its minor releases. Depending on your specific needs and requirements, you might want to update your software version, although it is usually not as urgent as security updates.
- Risk Assessment. Running outdated OpenSSL versions can pose risks. Factors such as the sensitivity of the data you are handling, the potential impact of a security breach, and the likelihood of exploitation can help you decide how often you want to update your software.
Conclusion
You now know how to check the OpenSSL version on your system. The data from the command output can be used to improve server security, troubleshoot errors, or submit a bug request.
Next, see how to generate CSR using OpenSSL, or check out our comprehensive tutorial on OpenSSL.