The healthcare sector has embraced digitalization as an indispensable tool for managing patient data and delivering healthcare services more efficiently. Digitalization allows healthcare providers to maintain comprehensive, portable, and easily accessible electronic records. Such accessibility ensures that medical histories, test results, prescriptions, and treatment plans are readily available, enhancing the quality and continuity of care.
While these technological advances have brought numerous benefits, they have also opened the door to cyber attacks targeting computer systems and the invaluable data they store. Recognizing the continuously changing threat landscape is our foremost defense against cybercrime.
This article provides an overview of the current threats to healthcare cybersecurity and the steps you and your organization can take to mitigate them.
What is Cybersecurity in Healthcare?
Healthcare cybersecurity presents unique challenges, which stem from the sensitivity of patient data, regulatory requirements, and patient welfare. Consequently, healthcare organizations must adopt a specialized approach in addition to following general cybersecurity principles.
Cybersecurity breaches within healthcare often result in the postponement of critical medical procedures, putting lives at risk. Unlike other industries where the main concerns may be customer loss and reputation damage, healthcare is a matter of life and death.
Compounding the problem of healthcare cybersecurity is the fact that medical records are some of the most highly sought-after items on the dark web, commanding prices that range from $250 to $1,000. For reference, credit cards typically fetch an average of $100. Protected health information (PHI) is valuable to criminals as it clears the way for identity theft, medical fraud, blackmail, and extortion.
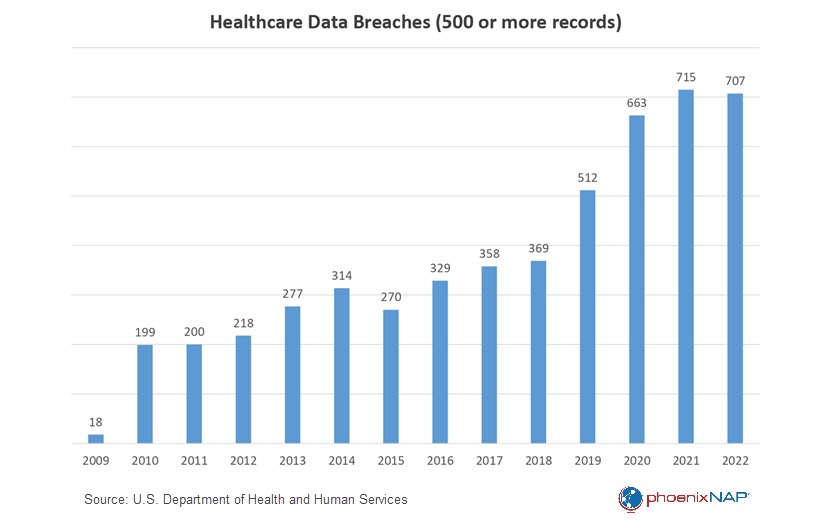
Cybersecurity Healthcare Statistics
Cyber attacks pose an ever-growing threat to critical infrastructure sectors. Among these, the healthcare industry is particularly vulnerable. According to the latest IBM report, the average cost of a healthcare breach in 2023 surged to nearly $11 million, a 53% increase from 2020. This figure is significantly higher than the average cost of a data breach across all industries, which is $4.45 million.
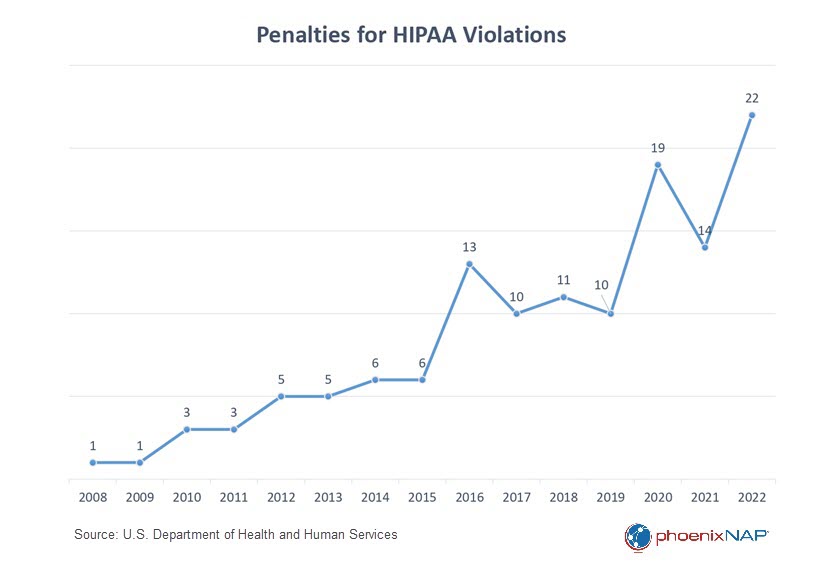
Here are notable healthcare cybersecurity statistics derived from authoritative data gathered by the U.S. Department of Health and Human Services (HHS).
- Over the past three years, the cost of healthcare data breaches has gone up by 53.3%.
- In 2022, there were 11 healthcare data breaches affecting over 1 million records and 14 breaches impacting more than 500,000 records. 71% of these breaches involved hacking and ransomware. Over the past five years, the occurrence of mega breaches, affecting over one million records, has almost doubled.
- The average data breach involving one million compromised records costs healthcare organizations almost $40 million.
- Hackers are increasingly focusing on the business associates of healthcare providers. Throughout 2022, business associates independently reported 127 data breaches. Furthermore, an additional 394 reported breaches involved business associates, representing a remarkable 337% increase since 2018. The year 2022 marked the first instance where data breaches reported by business associates exceeded those reported by healthcare providers.
- Specialty clinics have experienced a notable increase in data breaches, rising from 20% of all healthcare data breaches in 2019 to 23% in 2021 and 31% in 2022. Meanwhile, hospital systems follow closely at 29.6%.
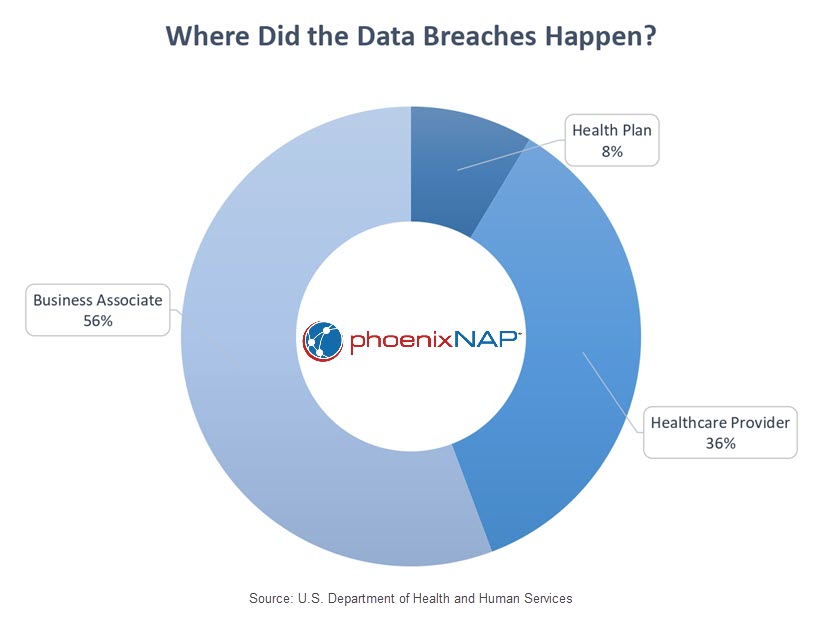
Healthcare Cybersecurity Threats
Healthcare Cybersecurity Threats encompass a broad spectrum of intentional malicious acts and inadvertent accidents from various internal and external sources.
Here are the primary cybersecurity threats facing the healthcare sector:
Social Engineering
Social engineering attacks use manipulative tactics to exploit human psychology and deceive individuals into revealing sensitive information, such as passwords or personal data.
Attackers assume false identities and manipulate potent emotions like greed or fear to trick victims rather than resorting to sophisticated hacking. For example, they may send multiple emails to establish trust and pose as someone the victim knows, like an IT help desk representative from their company.
Additionally, many attackers exploit ongoing events to create a sense of urgency and impersonate high-ranking figures within an organization. Worryingly, this attack vector has become increasingly polished and effective in recent years.
Here are some common methods of executing a successful social engineering attack:
Phishing Emails
A prevalent form of social engineering, phishing emails typically contain deceptive links or files that appear to originate from trustworthy sources, such as colleagues or managers. However, clicking these links downloads malicious software and gives unauthorized access to the victim's computer or network. Despite being a longstanding and widely recognized tactic, phishing emails are still the primary point of compromise in approximately 60 percent of healthcare data breaches.
Most phishing attacks cast a wide net to trap as many victims as possible. On the other hand, spear phishing is more focused and personally attacks specific individuals or organizations. The attackers often scrape data from social media, blogs, email newsletters, or previous leaks to obtain details about the target and gain their trust.

Employing email security best practices can significantly reduce the risk of falling victim to most phishing attacks.
Baiting
Baiting is a social engineering tactic used in digital and physical contexts that relies on greed to compromise security systems.
For example, physical baiting often involves strategically placing devices loaded with malware or spyware in public spaces. Unsuspecting victims may think they've found a free USB drive, but when they plug the device into their computers, they unknowingly download malicious software onto their hard drives.
On the other hand, digital baiting usually involves ads that promise attractive deals but redirect victims to websites that immediately trigger malware downloads. Another common tactic is disguising malicious programs as legitimate software or updates.
Tailgating
Tailgating is a social engineering method in which an unauthorized person enters a restricted area by following an authorized person through a secured door. The unauthorized person may pretend to be a legitimate employee or delivery person or simply ask the authorized person to hold the door open for them. Once inside, the attacker can access sensitive information and systems or install malware.
Despite its simplicity, tailgating is surprisingly effective – especially when combined with other social engineering techniques. An example of how successful tailgating can be is the story of Frank Abagnale, the protagonist of the film "Catch Me If You Can." He would often pose as a doctor, using tailgating to gain access to restricted areas.
Scareware
Scareware is a type of social engineering attack that exploits fear to trick users into giving up their personal information or downloading malware.
Often appearing as a pop-up window or a fake antivirus program, scareware often warns the user that their computer is infected with malware and demands they pay a fee to remove it. If the user falls for the trick, they may give up their personal information or download additional malware, which can compromise their device and the entire network.
Pretexting
Pretexting is a social engineering technique that preys on people's trust in institutions. Attackers often pose as legitimate government officials or law enforcement officers to trick the victim. Fake emails or websites that look legitimate are also a common method.

In 2019, a UK energy firm fell for an AI deepfake social engineering attack, losing €220,000. The criminals used AI voice emulation to impersonate the CEO, convincing the company to send money to the scammer's account. To find out more, read our article 15 social engineering examples.
Ransomware
Ransomware is malicious software that denies users access to their data. It achieves this by encrypting the data with a key known solely to the attacker deploying the malware. The victim is then instructed to pay a ransom, often in cryptocurrencies like Bitcoin or Monero, to obtain the decryption key necessary to regain access to their data.
Ransomware typically leverages one type of threat to establish a foothold and exploit vulnerabilities in a system. For instance, successful phishing attacks can lead to the installation of ransomware. After infiltrating a system, ransomware has the potential to spread via lateral movement within a network or to other linked devices. Certain ransomware variants possess worm-like functionalities that enable them to traverse vulnerable systems autonomously without user interaction.
Typically, ransomware remains concealed in the background to evade detection, sometimes for months, allowing attackers to monitor their victims and plot their attack. This strategy may include disrupting routine backup schedules, rendering backups useless. Some ransomware attackers even steal data before encrypting it on the victims' systems. If a victim refuses to pay, attackers may threaten to publicly disclose or sell the stolen data to third parties – a technique known as double extortion.
Healthcare organizations are particularly vulnerable to ransomware because they must follow strict rules to protect patient privacy. If they fail to do so, they can be fined by the HHS, incentivizing hackers to threaten to reveal the breach publicly.
Paying a ransom does not guarantee that the attacker will decrypt or unlock the compromised data, even if they promise to do so. Attackers often tailor the ransom amount based on an organization's perceived ability to pay. Sometimes, they assess an organization's cyber insurance policies and set the ransom amount to match the policy limit.
In 2022, healthcare organizations exhibited the highest willingness to pay the ransom, with approximately 61% of ransomware incidents resulting in payments. Surprisingly, despite their readiness to meet hackers' demands, the healthcare industry recorded the lowest average ransom amounts across all sectors, with an average ransom of about $197,000.
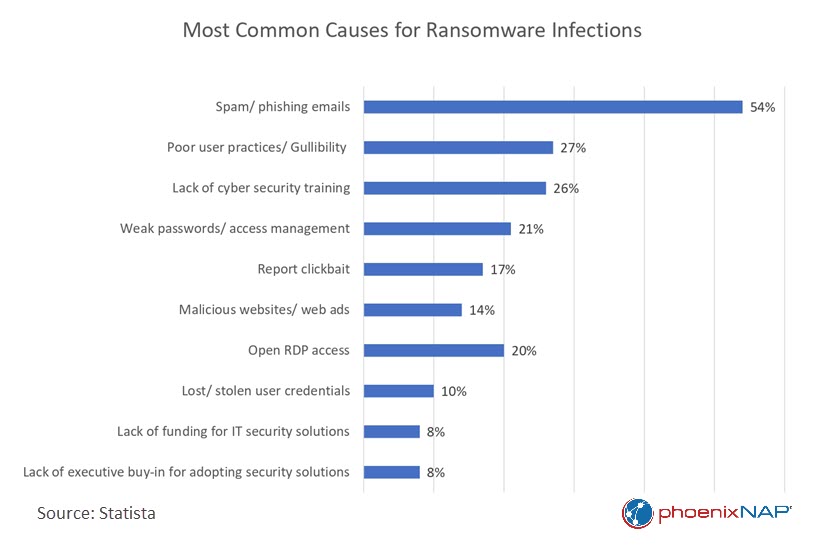
In 2022, approximately 66% of U.S. hospitals experienced a ransomware attack, marking a nearly 50% increase compared to 2021. Explore our article on ransomware in healthcare for vital insights on protecting your organization.
Equipment Theft and Data Loss
The loss or theft of mobile devices, including laptops, tablets, smartphones, and USB drives, is an ever-present threat that can place sensitive data in malicious hands. While the monetary value of the lost device is one aspect, the ramifications of a work device containing sensitive data falling into the wrong hands are far-reaching.
If lost devices lack strong protections like two-factor authentication or encryption, there's a higher chance that someone unauthorized could access, share, or use sensitive information inappropriately. The data may be erased or irrevocably lost even if you eventually recover the device. Such losses can disrupt business operations, compromise patient safety, and necessitate notifying affected patients, the HHS, and possibly the media.
These concerns are further compounded in the context of BYOD (Bring Your Own Device) policies. If employees use their mobile devices to access and handle sensitive patient data, extending security measures to personal devices is essential to mitigate the risks associated with potential loss or theft.
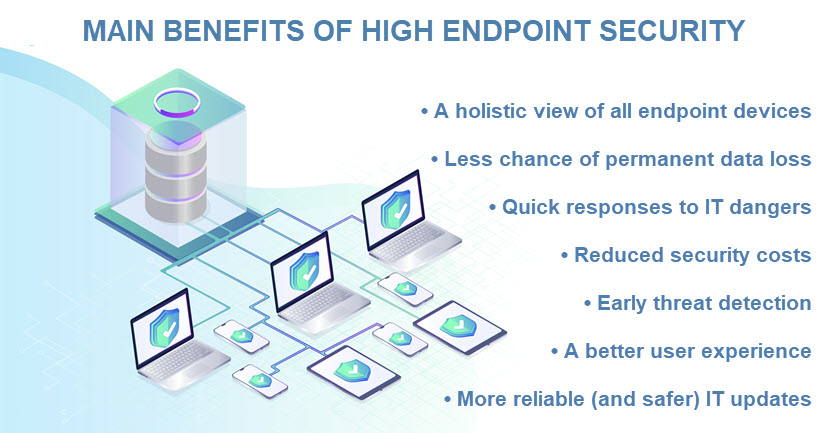
Robust endpoint security helps prevent data loss by encrypting devices, enabling remote wiping, and providing geolocation tracking for lost or stolen devices. It also ensures access control and monitors inventory to minimize theft-related data breaches.
Insider Threats
Insider threats involve individuals who possess legitimate access to an organization's computer systems and networks. These threats lurk within every organization where employees, contractors, or other users hold access to the organization's technological infrastructure, networks, or databases.
Insider threats can manifest in two primary forms: accidental and malicious.
Accidental Insider Threats
Accidental insider threats, while non-malicious, stem from negligent actions or honest mistakes. These may include falling victim to deception, procedural errors, or lapses in diligence. An employee unintentionally sending large volumes of PHI to an incorrect recipient exemplifies an accidental insider threat.
Malicious Insider Threats
In stark contrast, malicious insider threats are characterized by deliberate actions that aim at personal gain, extortion, or harm to the organization or individuals within it. These threats are orchestrated by employees, contractors, or other users with access to the organization's resources. A common example of a malicious insider threat is a disgruntled employee with access to patient records who begins printing extra copies and selling them on the dark web.
Attacks on Network-Connected Medical Devices
Network-connected medical devices harness networking protocols, such as Bluetooth, TCP/IP, and others, to facilitate communication and transmission of clinical information. The range of medical devices is broad, encompassing everything from simple tongue depressors and bedpans to intricate programmable pacemakers and closed-loop artificial pancreas systems.
In a dramatic scenario, cyber attackers successfully breach a healthcare provider's computer network, gaining control over a critical server. As a result, they gain control of all the heart monitors within an intensive care unit, putting lives in danger.
What makes this situation even more frightening is the potential use of highly sophisticated malware that can manipulate medical images to the extent that even vigilant medical professionals might fail to detect these alterations, even when they receive alerts. This example vividly illustrates the vulnerabilities associated with network-connected medical devices and the severe risks they pose when compromised.

Healthcare Cybersecurity: Best Practices
There are key differences between healthcare and general cybersecurity best practices due to the healthcare industry's unique nature.
Chief among them is that healthcare organizations must adhere to the Health Insurance Portability and Accountability Act (HIPAA), a U.S. federal law that mandates additional security and privacy measures that do not apply to other industries. These measures primarily relate to protecting vast amounts of patient data with strict controls over electronic health records.
Here are the best practices to address the unique challenges of safeguarding protected health information.
Create a Cybersecurity Culture
According to Verizon, the human factor contributes to 74% of all breaches, while the 2021 State of Privacy and Security Awareness Report states that approximately 24% of U.S. healthcare employees have not received cybersecurity awareness training.
Cybercriminals employ social engineering and phishing attacks to exploit individuals, tricking them into clicking malicious links or attachments. That is why cultivating a robust culture of internal training is paramount for fortifying cybersecurity within healthcare organizations. This culture should permeate all staff members, including contractors and part-time employees, who work to ensure that PHI is protected at every stage, whether in storage, transit, or at rest.
Healthcare organizations must also maintain records of completed training sessions as the governing body of HIPAA, the HHS, may request access to training records from the past 3 to 4 years during a HIPAA audit.
Hackers can use easily discoverable personal information like your high school to reset passwords and answer security questions. Strong passwords make it significantly harder for them to guess your credentials.
Enable Swift Backup and Recovery
Patient data is at the core of operations in the healthcare industry, and any disruption can have far-reaching consequences. Whether it's a cyberattack, system failure, or unexpected downtime, the ability to bounce back swiftly and securely is a non-negotiable requirement.
Quick and effective backup and recovery procedures enable you to restore systems to a previous, unaffected state in case of data loss or system compromise – reducing downtime to a minimum. Additionally, backups protect against ransomware by providing a way to recover data without paying a ransom.
phoenixNAP's backup and recovery solutions use cutting-edge technologies that secure your essential workloads, ensuring they remain accessible around the clock. Our global cloud infrastructure is supported by top-tier systems that deliver optimal protection with versatile implementation choices.
Adopt a Holistic Approach to Security
Physical and digital security are often seen as separate fields, but they are two sides of the same coin. Due to the increasing interconnection of systems and devices, physical breaches often lead to cybersecurity breaches and vice versa.
Here are some proven strategies for reducing equipment theft and lowering cybersecurity risk:
- Entry Restriction: Mandate using keycards, biometrics, and PIN codes for entry into sensitive areas of your organization.
- Surveillance: Install security cameras to monitor and deter unauthorized access.
- Alarms and Sensors: Use motion detectors, window and door sensors, and alarms to alert you to illicit entry.
- Locks and Safes: Secure valuable equipment and documents in cabinets, safes, or rooms sealed with high-quality locks.
- Inventory Management: Maintain and regularly audit a detailed inventory of equipment, including serial numbers.
- Asset Tracking: Implement asset tracking technology to monitor the location and status of valuable equipment.
- GPS and Remote Locking: For mobile devices and laptops, use GPS tracking and remote locking tools to locate and secure devices if they are lost or stolen.
Minimize Insider Threats
Preventing disgruntled employees from becoming a cyber risk is a challenge with no clear-cut solution. People are complex and unpredictable, often driven by diverse motives. It's not possible to please everyone all the time.
Nevertheless, implementing the following strategies can help reduce the likelihood of discontent among employees and foster a secure and productive workplace.
Establish a Whistleblower Program
Develop a system that allows employees to confidentially report concerns about their colleagues' behavior or potential security threats. Whistleblower programs promote vigilance and provide a valuable channel for discreetly identifying and addressing potential threats.
Foster Open Communication
Encourage a workplace environment that promotes open and honest communication between employees and management. When people feel comfortable expressing concerns or doubts, it creates an atmosphere in which issues can be identified and addressed.
Solve Workplace Issues Quickly
Early intervention is crucial in preventing minor workplace issues from escalating into major problems. Implement clear processes and procedures for addressing and resolving conflicts, disputes, or grievances within your organization. Proactive handling of these issues can help prevent trouble further down the line.
Implement a Comprehensive Exit Procedure
When employees leave your organization, it's crucial to have a robust exit procedure in place. The exit procedure should encompass administrative tasks such as revoking access privileges and collecting company property. Equally important is ensuring that no sensitive data remains on personal devices or cloud accounts. A thorough exit procedure minimizes the risk of data theft or unauthorized access by departing employees.
Protect Your Network-Connected Medical Devices
To address the vulnerabilities associated with network-connected medical devices, healthcare providers should implement the following strategies:
- Network Segmentation: Segment the network to create distinct zones, separating critical patient monitoring and medical device traffic from non-medical systems. This limits the attack surface and prevents unauthorized access.
- Access Management. Implement strict access controls, including zero-trust policies, to ensure only authorized personnel can interact with medical devices and critical servers. Utilize role-based access and strong authentication methods like biometrics or smart cards.
- Regular Software Updates. Stay vigilant in applying security patches and updates to all network-connected medical devices. Manufacturers should provide timely patches for known vulnerabilities.
- Intrusion Detection and Prevention. Deploy intrusion detection systems to monitor network traffic and detect suspicious activities. Automated alerts can prompt immediate responses to potential threats.
- Incident Response Plan. Develop a comprehensive incident response plan specific to medical device breaches. Define roles and responsibilities to ensure swift action in case of an attack. Regularly test and update the plan.
Consider Managed Security Service Offerings
In the healthcare industry, compliance is a necessity. However, ensuring compliance is a complex task due to several challenges. One major hurdle is finding, retaining, and affording skilled security staff. Healthcare security professionals are in high demand, making them expensive to hire and challenging to keep within an organization.
Organizations often turn to managed security service providers (MSSPs) to address this issue. These services can both enhance in-house tech solutions and supplement existing security staff, providing expertise and support that may be hard to find otherwise.
Here are some examples of what an external cybersecurity partner can provide:
- 24/7 monitoring of unusual data traffic, potential threats, and suspicious patterns.
- Immediate response to security incidents, including breach attempts and data leaks.
- Investigating the incident, containing the threat, and mitigating potential damage.
- Regular assessment of your systems and applications for vulnerabilities.
- Ensuring your systems are up to date with the latest security patches.
- Learning from each incident and analyzing past incidents to continually enhance detection capabilities and security posture.

Our HIPAA-ready hosting solution is built with compliance at its core, prioritizing security and privacy to align seamlessly with the requirements of the healthcare sector. We provide unmatched protection for sensitive health information by employing robust encryption protocols, strict access controls, and a comprehensive data backup and recovery infrastructure.
Conclusion
Cybersecurity incidents are very costly financially and otherwise. In addition to the direct costs of a data breach, there are indirect costs such as loss of productivity, damage to reputation, legal fees, and HIPAA fines and penalties. Ultimately, it can take years for an organization to recover from a cyber attack. Therefore, investing in healthcare cybersecurity is a financially smart choice that ultimately pays for itself.



