Managing access to the Linux operating system and its resources is an essential administrative task. Incorrectly set user permissions are a security vulnerability and, in some cases, may render the Linux system inoperable.
Find out how to administer user and service accounts in Linux and ensure your system's integrity and security.
Types of User Accounts in Linux
The following table provides an overview of user account types in Linux, their access levels, and uses:
| Account Type | Access Level | Usage |
|---|---|---|
| Root User | Access to the entire Linux system. Root users can initiate any command, modify system settings, edit files, or install software without restrictions. | Primarily used to perform system administration tasks. |
| Standard User | User privileges are limited. Standard users cannot perform actions that affect core system settings or other user accounts. | Basic access for utilizing various system resources. |
| Sudo User | A standard user who has been granted permissions to execute certain commands as the root user. | Every command that requires root privileges must be preceded with the sudo command. |
| System Account | User accounts for applications or automated services that need to perform specific tasks on the Linux system. | System accounts operate with restricted permissions to enhance security and control over system operations. |
| Guest User | Temporary accounts with restricted and controlled privileges. | Users that need access for a limited time and do not require personal files and settings. |
| User Groups | Permissions are assigned to a collection of users who are organized into logical groups with identical permissions. | Admins can manage permissions for an entire user group instead of managing individual user accounts. |
Understanding User Management Files
Linux stores user and group data in specific files and directories that contain user account info, passwords, and group configurations. System administrators can interact with these files to control and modify user and group settings in Linux.
The main files and directories for storing user data in Linux include:
- /etc/passwd. The passwd file contains a list of user accounts and the corresponding user ID, group ID, home directory, and the default shell. It is readable by most users, but only root and sudo accounts can add new users or remove and modify existing user data.
- /etc/group. The group file contains a list of user groups. Each line in the file represents a group and displays the group name, GID, and group members. Administrators can interact with this file to manage settings for an entire collection of users.
- /etc/sudoers. The sudoers file specifies which users have elevated permissions, on which machines, and for which directories. Admins can use this file to configure permissions for users and groups to use the sudo command.
- /etc/shadow. The shadow file stores encrypted user password information and other password-related data such as the password expiration date, last change date, and account expiration date. It is only accessible by the root user or users with appropriate privileges. The restricted access and encryption add another security layer compared to the /etc/passwd file.
- /etc/gshadow. The gshadow file stores encrypted user group password information and other password-related data such as the password expiration date, last change date, and account expiration date. Like the shadow file, it is only accessible by the root user or users with appropriate privileges.
- /etc/skel. The skel directory contains default configuration scripts and templates such as .bashrc and bash_profile. The templates are copied to the user's home directory when a new user is created, streamlining the provisioning of new user accounts.
- /etc/login.defs. The login.defs file contains system-wide user account policy settings, like the password aging policy. System administrators can refer to and modify this file to enforce specific security and user management rules.
Editing user management files directly is not recommended, as potential errors may compromise system security and integrity.
Linux User Management Commands
Command-line tools are the preferred method for managing users and groups in Linux. They have built-in checks and balances that ensure system security and consistency.
Follow the sections below for command examples.
Check Currently Logged Users
The most efficient way to determine which users are currently logged in a Linux system is to use the who command. Enter the following command to list currently logged users:
who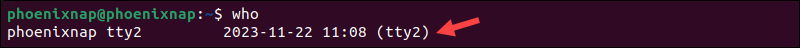
The terminal displays the user session information in several columns. Add the -H option to display the header of each column:
who -H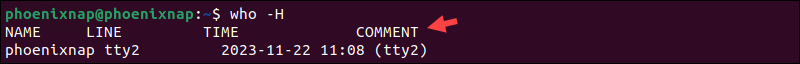
The headers describe what the data in each column represents.
List All Users
The /etc/passwd file contains data about all users on the Linux system. Several Linux commands, like cat, awk, and getent, can be used to display user data in the terminal.
Enter the following command to list Linux users:
cat /etc/passwd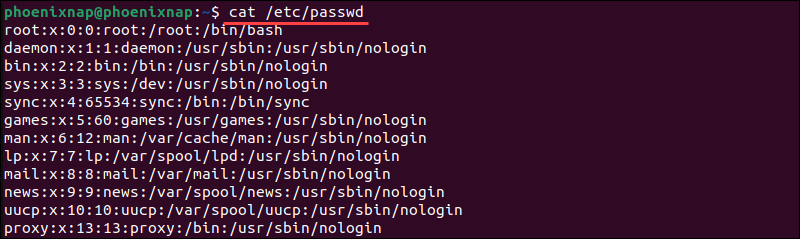
The system lists all Linux users and includes additional information, such as the user's default shell and home directory.
Alternatively, you can use the more and less command to display the file on several pages, allowing you to search and scroll through the list.
Create User (useradd/adduser)
The useradd command is used to create a new user in Linux. It requires root or sudo privileges.
Use the following command to add a new user:
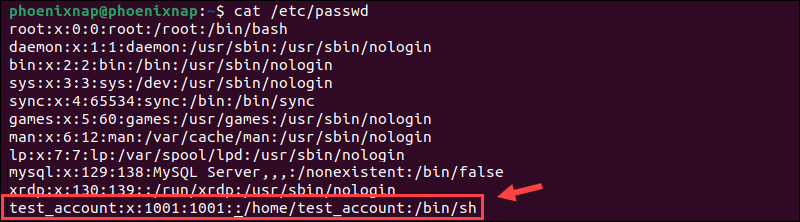
sudo useradd test_accountReplace test_account with the actual username you want to add. The system does not provide any output.
You can utilize the cat command to verify if the new user is visible in the /etc/passwd file.
Users can also be added via an interactive prompt with the adduser command. This command automatically creates a home directory for the user, sets a default shell, and prompts the user to enter a password to unlock the account.
Enter the following command to create an active user account in Linux:
sudo adduser test_account2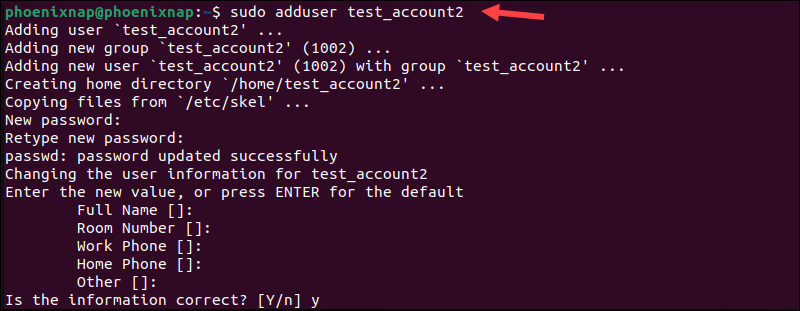
The command triggers a prompt that guides you through the creation process in an interactive interface.
Note: Learn more about the differences between useradd and adduser.
Modify Default User Settings (usermod)
The usermod command in Linux is used to modify various attributes of an existing user account. Administrators can utilize several options with this command to change specific data points:
-d- Changes the user's home directory.-s- Changes the user's default shell.-e- Sets an account expiry date.-c- Adds a comment to the user's entry.-u- Changes the user's UID (User ID).-aG- Adds the user to supplementary groups without removing existing group memberships.
In the following command, the -d option is used to change the location of the user's home directory:
sudo usermod -d /var/test_account test_account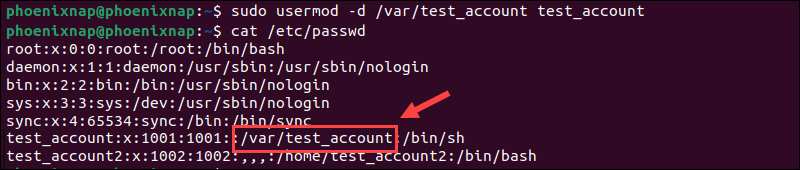
In this example, the home directory for the test_account user was changed from /home/test_account to /var/test_account.
Delete User (userdel)
The userdel command removes a user from the /etc/passwd file. For example, to delete the user test_account2, enter the following command:
sudo userdel test_account2Replace test_account2 with the actual username you want to remove. userdel does not automatically remove the user's home directory or other related files.
You can use the -r option to remove the home directory and mail spool:
sudo userdel -r test_account2Note: This action is irreversible, especially when using the -r
Typically, the system does not provide output to confirm the removal of the user.
Linux User Group Management Commands
User groups in Linux streamline the management of permissions and access rules for a collection of user accounts. Modifying a group's permissions or access rights will apply those changes to all users within the group.
Create Group
Enter the following command to create a new user group in Linux:
sudo groupadd test_groupReplace test_group with the name of the group you want to create. Use the getent command to confirm the new group is in the Linux /etc/group file:
getent group test_group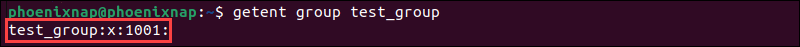
This command displays the details of test_group, including its name and ID.
How to Add or Remove Members From Group (usermod)
When you add a user to a group, they automatically receive the permissions associated with that group. In a Debian-based system, you can utilize the adduser command to add a user to an existing group:
sudo adduser test_account test_group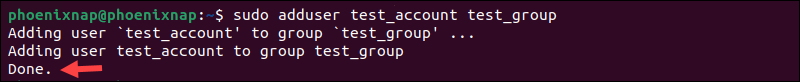
The system confirms that the action has been completed.
Use the usermod command with the -a (append) and -G (groups) options to append a user to an existing group while keeping them in their current groups:
sudo usermod –aG test_group test_account2Confirm if the user has been added by using the groups command:
groups test_account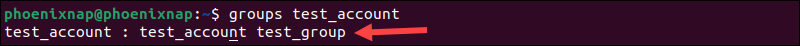
To remove a user from a specific group, use the deluser command:
sudo deluser test_account test_group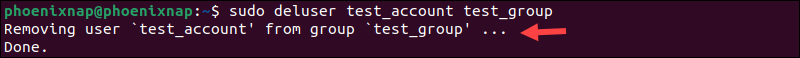
The system confirms that the user was removed from the group.
Display All Groups a User Is a Member Of (id)
Enter the id command to list the groups an individual user is a member of:
id test_account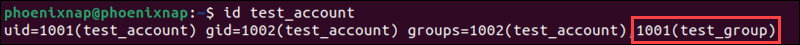
The -n and -G options instruct id to only list group names instead of numeric IDs.
id -nG test_account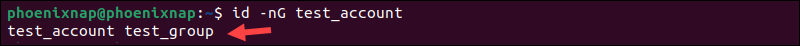
This command shows all the groups a user is a member of, including their primary and supplementary groups.
List all Groups and Members
The data about user groups is stored in the /etc/group file. Enter the following command to retrieve the names of all user groups, group IDs, and group members from the file:
getent group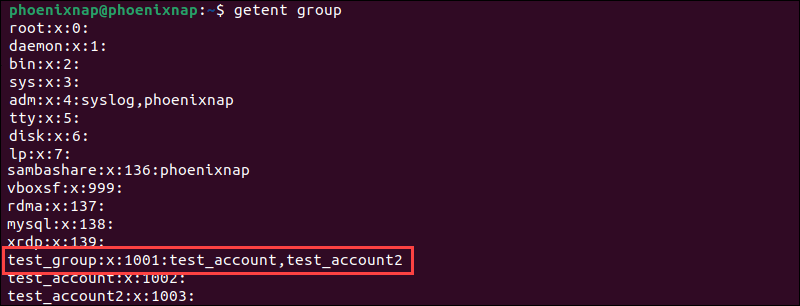
You can parse this list to extract group members using a tool like awk:
getent group | awk -F: '$4 != "" {print $1 ": " $4}'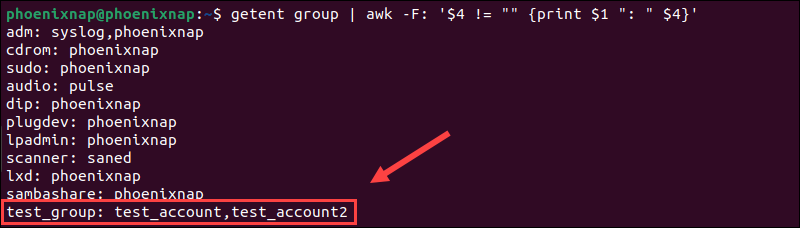
This command only lists groups with members followed by the individual member's usernames separated by commas.
Conclusion
You now understand the various types of user accounts in Linux, including their specific roles, access levels, and permissions. Use this information to manage users and groups effectively and avoid potential security risks and operational issues.
Refer to our comprehensive Linux Commands guide, which includes a handy, downloadable cheat sheet to assist you with your daily tasks.