Social engineering exploits the weakest link in any system: human error. It involves manipulating human psychology and behavior to deceive people into divulging sensitive information or granting unauthorized access to networks, systems, and physical locations.
Social engineering relies on exploiting powerful and near-universal emotions such as greed or fear instead of relying on technical hacking. It has even become the preferred tactic among hackers, and its impact on cybersecurity cannot be overstated.
This article lists the 15 most famous cyber attacks where social engineering was the predominant factor. By understanding the hackers' tactics, you will be able to identify and thwart social engineering attacks on you and your organization.
Social Engineering Examples
Let's look at some of the most infamous social engineering cyber attacks in history.
1. Kevin Mitnick's Early Career
In 1994, Kevin Mitnick successfully posed as an employee and convinced the technical support staff of Motorola, Novell, Nokia, and Sun Microsystems that he urgently needed access to certain information for troubleshooting. Through a combination of charm, technical jargon, and urgency, he persuaded the support staff to provide him with the information he needed.
Armed with sensitive technical details, Mitnick gained unauthorized access to internal systems and exploited the vulnerabilities he had learned about. He was caught, but after his release from prison in 2000, Mitnick said he considered his actions "simple crimes of trespass." He further explained that his motivation was only to learn how phone networks operated.
Later in life, Kevin Mitnick, who passed away in July 2023, used his talents for ethical hacking, becoming a respected security consultant and author.
2. Spear Phishing Attack on the Democratic National Committee
During the 2016 U.S. presidential campaign, a cyber attack targeted high-ranking officials and employees within the Democratic National Committee (DNC), the governing body of the Democratic Party in the United States.
The attackers crafted personalized and convincing phishing emails, a technique called spear phishing. Once a target clicked on malicious links or downloaded malware-infected attachments, they inadvertently provided their login credentials or allowed malware access to their system. The attackers gained unauthorized access to sensitive information within the DNC.
This breach eventually led to the release of confidential emails during the 2016 U.S. Presidential election campaign, which had significant political repercussions and triggered concerns about foreign interference. Investigations conducted by multiple cybersecurity firms blamed two notorious Russian hacking groups, "Fancy Bear" and "Cozy Bear," for the breach.
The DNC contacted cybersecurity firm CrowdStrike for coordinated remediation and disaster recovery services. Concerningly, their report said that the two Russian state-sponsored hacking groups had infiltrated the DNC's network as early as 2015.
3. Sony Pictures Hack
In 2014, a group known as "Guardians of Peace" (GOP) targeted Sony Pictures Entertainment with spear phishing emails masquerading as official communications from trusted sources. The GOP tricked Sony employees into disclosing their login credentials or clicking on malicious links that granted access to the company's systems.
Once inside, the hackers remained undetected for at least two months, during which they installed a listening implant, a backdoor, a proxy, a destructive hard drive tool, and a cleaning tool to remove traces of the attack. Subsequently, they exfiltrated vast amounts of sensitive data, including unreleased movies, confidential business documents, employee records, and private email conversations.
One of the most significant aspects of the data breach was the theft of several films, including Annie, Fury, and The Interview. The movies were leaked online before their official release dates, causing immense financial damage to the film studio as copies were spread across the internet.
The leaked emails were also particularly damaging, as they exposed unfiltered conversations between executives and other industry figures. Some of the emails contained candid opinions about celebrities, actors, and business partners.
While the identity of the individuals behind the GOP remains uncertain, the United States government pointed to North Korea as the likely culprit. The attack was allegedly motivated by the release of the film The Interview, a comedy centered around a fictional plot to assassinate North Korean leader Kim Jong-un.
4. Bangladesh Bank Heist
Contrary to the belief that bank robberies only happen in Western films, the Bangladesh Bank Heist was one of the most audacious and successful in history.
In February 2016, hackers targeted the central bank of Bangladesh. With help from insiders, they sent spear phishing emails containing malware-infected attachments. When their targets eventually opened these attachments, they granted the hackers access to the bank's network and systems.
Once inside, the attackers used internal processes and controls to manipulate the bank's SWIFT (Society for Worldwide Interbank Financial Telecommunication) system, a messaging network used by financial institutions to send and receive payments securely.
Using fraudulent SWIFT transactions, the hackers attempted to transfer nearly $1 billion from the Bangladesh Bank to their accounts in the Philippines. Although some of the transactions were blocked or reversed, the hackers were able to transfer approximately $81 million.
Law enforcement agencies are still working to catch all the perpetrators of the Bangladesh Bank robbery.

Research by Deloitte suggests 91% of all cyber attacks begin with a phishing email.
5. NotPetya
Ransomware is a program designed to extort money, and it ranges from basic lock screens to intricate code with encryption and data exfiltration capabilities.
Emerging in 2016, Petya is a ransomware strain that diverged from tradition by targeting the Master Boot Record (MBR) or the hard drive's partition table, rendering the entire system inoperable. Initially, Petya distributed its payload disguised as a PDF file, spreading through email attachments using various infection vectors like spear phishing emails and compromised websites.
On June 27, 2017, a major global cyber attack utilized a new variant of Petya. Kaspersky reported attacks on more than 80 companies, with 80% of all infections happening in Ukraine, while Germany was the second hardest-hit country with about 9%. The U.S. government estimates that the total damage caused by this attack exceeds $10 billion.
Experts believed this was a politically motivated and state-sponsored attack against Ukraine, as it primarily targeted the National Bank of Ukraine and coincided with the eve of the Ukrainian Constitution Day holiday.

6. Twitter Bitcoin Scam
In July 2020, hackers targeted several high-profile Twitter accounts, including those of Elon Musk, Barack Obama, Joe Biden, Kanye West, Bill Gates, and many others.
The attackers began by scraping LinkedIn to identify Twitter employees with administrator privileges. Using paid tools available to job recruiters, they accessed these employees' private contact information, including cell phone numbers.
Having selected their targets, they initiated contact by impersonating Twitter employees. The attack vector was connected to the company's remote work policy during the COVID-19 pandemic. The hackers managed to access the Twitter employees' Slack communications channel, where crucial information and authorization procedures for accessing the company's servers were pinned.
Once they breached the network, the attackers posted fraudulent tweets that deceived followers into believing that if they sent a specific amount of Bitcoin to a designated address, they would receive double in return.
The tweets were carefully crafted to appear authentic, capitalizing on the trust and authority of the targeted individuals. Many fell victim to the scam, sending their Bitcoin to the specified addresses and cumulatively losing hundreds of thousands of dollars.
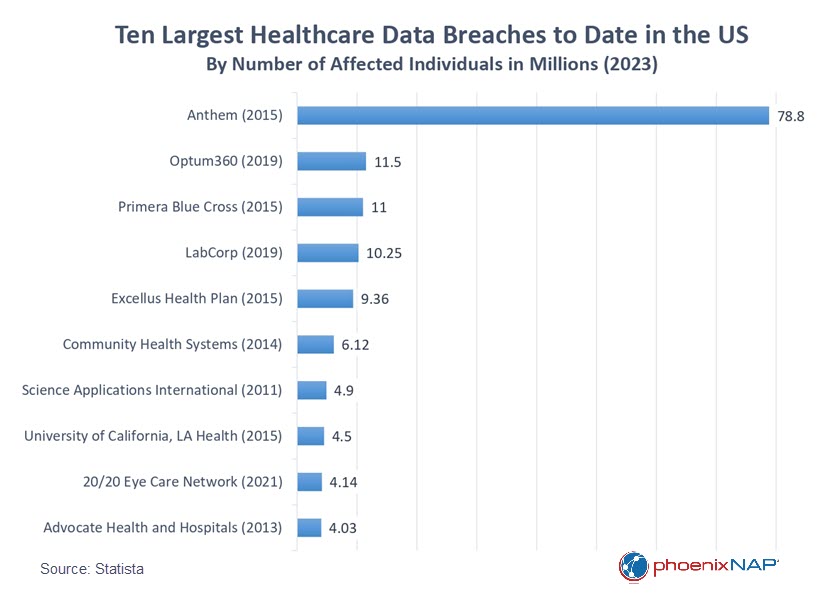
7. Anthem Data Breach
The Anthem data breach of 2015 was one of the most expensive and impactful phishing attacks in history.
Targeting one of the largest health insurers in the United States, the Anthem breach is the most extensive healthcare data breach ever recorded, giving the attackers access to the personal and medical information of nearly 79 million people. The stolen data included names, dates of birth, Social Security numbers, medical IDs, and other sensitive information, which were likely sold on the dark web.
The attack was extremely expensive for Anthem as well, costing them $230 million for remediation efforts. The aftermath of the attack required Anthem to allocate $115 million to settle lawsuits, $39.5 million to resolve the state attorney general’s investigation, and an additional $16 million to address the HIPAA audit and subsequent HIPAA violation fine.
A subsequent investigation led by government officials and the cybersecurity firm Mandiant claimed that the attack was state-sponsored but didn't name any perpetrators.
Healthcare organizations are particularly vulnerable to cyber attacks.
phoenixNAP's Data Security Cloud is purpose-built to meet the stringent requirements of the healthcare sector. With strong encryption, rigorous access controls, and comprehensive data backup and recovery solutions, we ensure unparalleled security for protected health information.
8. Target Data Breach
The Target data breach was one of the most significant in history, resulting in the compromise of over 40 million credit card numbers, addresses, and phone numbers. In the aftermath, Target was forced to pay an $18.5 million settlement to the victims of the breach.
The attackers breached Target's network by compromising a third-party vendor, a refrigeration contractor called Fazio Mechanical. This type of attack, known as a supply chain attack, focuses on exploiting the weakest link within a supply chain.
In 2022, the frequency of supply chain attacks exceeded that of malware-based attacks by 40%.
The Target hackers used phishing emails to install Citadel, a variant of the Zeus trojan, onto Fazio's computers. Using the breached vendor as a staging point, the hackers exploited an undiscovered vulnerability to gain a point of presence, escalate privileges, and attack Target's internal systems.
At the time of the breach, all major versions of enterprise-grade anti-malware were capable of successfully detecting Citadel. However, Fazio most likely relied on a free anti-malware solution that lacked real-time protection.
9. Evaldas Rimasauskas Wire Fraud
From 2013 to 2015, a Lithuanian called Evaldas Rimasauskas stole $99 million from Facebook and $23 million from Google by creating fake invoices. With meticulously crafted emails, he deceived the companies' employees into paying for goods they did not order or receive.
Using a technique similar to "typo squatting" or "URL hijacking," Evaldas created a company in Latvia with a name closely resembling Quanta Computer Inc., a reputable Taiwanese electronics manufacturer. Under this guise, he conducted fraudulent multimillion-dollar transactions with Google and Facebook, forwarding the funds to his bank accounts in Latvia and Cyprus.
To cover his tracks, he fabricated invoices, contracts, and letters bearing forged signatures of Google and Facebook executives and agents. Surprisingly, neither company scrutinized the legitimacy of these documents.
His fraudulent activities ended when Lithuanian authorities apprehended him in 2017, and he was subsequently extradited to the United States. Rimasauskas pleaded guilty to one count of wire fraud and was sentenced to 60 months in prison.
10. AI Deepfake Scam Hits UK Energy Firm
In 2019, criminals used AI voice emulation software to steal €220,000 from a UK energy firm in a textbook example of a whaling attack – a spear phishing attack against a high-level executive.
The scammers successfully impersonated the German CEO of the UK energy firm's parent company. The scammers persuaded the UK CEO to urgently send money to a Hungarian supplier, which was, in fact, their account.
Shortly after the UK CEO sent the €220,000, the hackers called again, claiming they had sent money to reimburse him for the urgent transaction. Later that day, they made a third call, once more impersonating the CEO and requesting a second payment.
The UK CEO grew suspicious as the reimbursement had not arrived, and the third call came from an Austrian phone number. Consequently, he decided not to proceed with the second payment.
Following the transfer to the Hungarian bank account, the funds were moved to Mexico and distributed to other locations.
During the investigation, it was concluded that the perpetrators had employed commercial software to impersonate the German executive's voice. This is one of the first known occurrences of AI voice mimicry being used for fraud.
To date, investigators have not identified any suspects and have had to end the investigation.

The widespread digitalization of most aspects of society defines our era. As cybercrime continues to rise, the importance of cybersecurity will only increase. To stay ahead of the curve, read our article on how to prevent social engineering attacks, featuring seventeen security experts.
11. Google Drive Scam
In 2020, a phishing scam weaponized push notifications to drive its victims to malware-riddled websites. Exploiting a flaw within Google Drive, scammers sent seemingly genuine push notifications and emails from Google, prompting Gmail users to click on the "Open in Docs" button in the email. Upon doing so, users were directed to an authentic Google-hosted page, where they were asked to grant permission to a seemingly legitimate service called "Google Docs" to access their email account data.
Unfortunately, providing permission granted the scammers access to the victim's email account, contacts, and online documents. The malware then automatically sent emails to everyone in the victim's contact list to further propagate itself.
While phishing is not a new tactic, the alarming aspect of this scam is that the emails and notifications originated directly from Google. Since the messages appeared legitimate, users were caught off guard.
Upon receiving victim reports, Google promptly removed the documents utilized in the scam and addressed the security flaw.
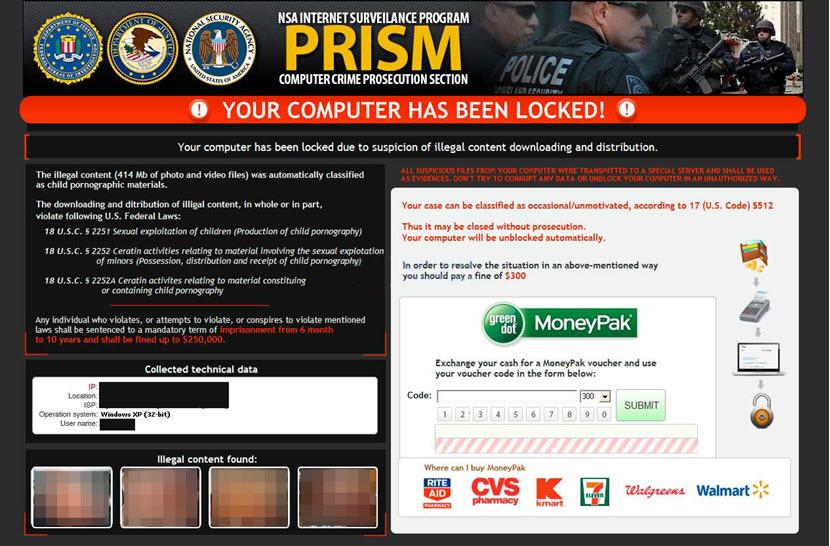
12. Reveton
In 2012, the Reveton ransomware strain gained notoriety as the first Ransomware-as-a-Service (RaaS) operation. It provided gangs with limited technical expertise, ransomware tools, and infrastructure with the means to conduct attacks without having to develop the malware themselves. Today, almost anyone can create highly effective malware campaigns, thanks to RaaS.
Another notable aspect of Reveton is its aggressive and intimidating approach. Nicknamed a "Police Trojan," it locked the victim's screen, displaying a fake message from law enforcement agencies, falsely accusing them of illegal activities such as copyright infringement or having a connection to child pornography.
To unlock the computer, the hackers demanded payment of a "fine," exploiting official logos and language to instill urgency and fear in the victim. In this aspect, Reveton serves as a prime example of hackers skillfully using social engineering to establish credibility.
Moreover, the ransomware utilized the user's computer IP address and webcam imagery to create the illusion of constant monitoring and recording, manipulating the victim into succumbing to the ransom demand.
13. The Lapsus$ Hacking Group
In late 2022, the UK police arrested two teenagers, Arion Kurtaj (18) and an unnamed 17-year-old, for their involvement in hacking various organizations. The long list of companies includes Nvidia, Rockstar Games, Revolut, BT Group, Uber, and even the cloud storage servers of the London Police.
The prosecutor assigned to the case emphasized that the hackers were not merely indulging in "juvenile pranks" but in sophisticated crime with the aim of profit.
The young hacker's resume includes the following:
- Stealing sensitive code and videos of Rockstar's latest Grand Theft Auto game and leaking the information while demanding a ransom. Kurtaj allegedly used social engineering to pose as a contractor within the company and breach the firewall.
- The pair accessed software building blocks for Nvidia's products, publicly releasing some of the stolen data and threatening to release the rest if they didn't receive a ransom.
- The teenagers also allegedly hacked BT and engaged in SIM swap fraud, draining the cryptocurrency and bank accounts of multiple customers.
While being astonishingly competent for someone so young, the pair had a penchant for bragging that eventually led to their demise. After boasting about their exploits online, the police quickly identified and arrested the hackers.
14. Barbara Corcoran Phishing Incident
In 2020, Barbara Corcoran, the host of the reality television series Shark Tank, was nearly scammed out of $400,000.
The scam was a phishing attack in which the scammer successfully deceived Corcoran's bookkeeper with an email that looked like it was from her assistant. The email asked the bookkeeper to wire money to a fictitious contractor working on a European renovation project.
As Corcoran herself remarked, "The story was totally plausible because I invest in a lot of real estate and do a lot of renovations for a living."
In a stroke of luck, the German-based bank the bookkeeper used to transfer the money froze the transaction before it reached the scammer's account in China. Corcoran explained that her bank in New York requested the German bank to suspend the transfer, allowing her to provide evidence of fraud.
15. Cabarrus County Hack
In 2018, hackers successfully persuaded Cabarrus County, NC officials to give them more than $2.5 million.
Posing as representatives from a construction contractor, the scammers contacted officials, pretending to be involved in the construction of a local high school, which was genuinely being built. They skillfully convinced the officials to change the bank account to which they made payments for the construction of the school. To strengthen their deception, they provided what appeared to be legitimate documentation and approvals.
Once the criminals received the deposit, the funds were rerouted through various other accounts. Several weeks later, the scheme came to light when the genuine vendor contacted the officials, inquiring about a missed payment.
The authorities eventually recovered a portion of the funds, reducing the damage to 1.7 million.

How to Defend Against Cybercrime
The first line of defense against cybercrime is having a strong password and following email security best practices. Just following these common-sense procedures would have made the difference between getting hacked or not in many of the examples listed above.
As the sophistication of the attackers has grown, so has the technology used to thwart them. AI-assisted intrusion detection systems and firewalls stand at the forefront of defense against modern cybersecurity threats. They can analyze vast amounts of data, detecting anomalies, patterns, and breaches in real time.
In the End, It's All About the People
As impressive as these technologies are, they cannot single-handedly shield us from determined criminals. By prioritizing cybersecurity training for employees, organizations build a robust human firewall that fortifies their defenses and creates a united front that stands as a bulwark against potential cyber threats.



