Hybrid clouds are highly advantageous but challenging to keep safe. Continuous data movement and tight integration between on-prem and cloud computing components create ample room for vulnerabilities. Organizations require a proactive security mindset and various precautions to protect their hybrid clouds reliably.
This article covers the essentials of hybrid cloud security and ensures you're ready to take on the task of protecting your IT environment. We discuss the most common challenges companies face when securing a hybrid cloud and present 10 tried-and-tested methods for improving hybrid cloud security.
Learn about the main >benefits and >challenges of hybrid clouds to evaluate whether this deployment model is the right choice for your business.
What Is Hybrid Cloud Security?
Hybrid cloud security is an umbrella term for various measures and practices designed to protect data, applications, and infrastructure within a hybrid cloud. The main goal is to ensure resource confidentiality, integrity, and availability across integrated on-prem and cloud environments.
Hybrid clouds pose unique security challenges because they combine concerns of on-site systems and cloud services. Organizations must secure each component of the hybrid model individually and ensure that the system is safe at the junctions between different IT environments.
High levels of security are essential to the success of the hybrid cloud deployment model. Here's what organizations get by boosting hybrid cloud security:
- Reduced attack surface. An adequately secured hybrid cloud provides attackers with fewer ways to breach the system and set up a foothold.
- Data integrity. High levels of hybrid cloud security ensure the integrity and confidentiality of sensitive data.
- Operational resilience. Robust security measures help avoid system downtime. Organizations get to maintain business continuity even in the face of disruptive incidents.
- Cost-efficiency. Effective security strategies lead to significant cost reductions. Organizations reduce the risk of costly data breaches, improve uptime, and optimize resource utilization.
- More reliable compliance. Robust hybrid cloud security helps companies comply with strict data protection regulations like CCPA or GDPR.
Proactively planning for security is one of the essential initial steps when creating a well-rounded >hybrid cloud strategy.
What Are Hybrid Cloud Security Challenges?
Hybrid clouds pose unique security challenges due to the complexity and diverse nature of these IT environments. Below are the most common challenges of hybrid cloud security.
Data-Related Concerns
Adopters of hybrid clouds must decide which data sets belong within private data centers and which should reside in public or private clouds. Choosing the correct placement for each data set and deciding how to keep it safe is a major challenge of hybrid cloud security.
Continuous data transfers further complicate this issue. Data within a hybrid cloud must move between on-prem servers and cloud environments for processing, storage, backup, or disaster recovery purposes.
When data is in transit between on-prem and cloud systems, files are vulnerable to:
- Interceptions and eavesdropping.
- Man-in-the-Middle (MitM) attacks.
- File modification or tampering.
- Data replay attacks.
- Packet sniffing and traffic analysis.
- DNS spoofing and cache poisoning.
Security aside, adopters must also deal with the challenges of data synchronization, version control, and data validation. Additionally, organizations operating in regulated industries must adhere to specific data storage and movement compliance requirements.

Interoperability Issues
Interoperability challenges arise due to a hybrid cloud's need to integrate and operate seamlessly across diverse IT environments. Efficient and safe operations require smooth interoperability between on-site infrastructure and cloud-based services.
Hybrid cloud strategies often combine multiple types of public cloud services (IaaS, PaaS, and SaaS), frequently belonging to multiple providers. Each vendor has its own:
- Security protocols.
- Set of services.
- APIs.
- Networking configurations.
- Management interfaces.
The lack of standardized protocols complicates security efforts. Organizations often need to develop custom solutions to facilitate communication and data exchange between on-premises servers and the cloud. Divergent models and controls introduce vulnerabilities if not correctly aligned.
As an extra issue, interoperability problems often impact the overall performance of hybrid cloud environments. Delays in data exchange, increased latency, and reduced efficiency are common problems.
Increased Attack Surface
Hybrid clouds have an amplified attack surface due to the combination of public clouds, on-prem infrastructure, and private clouds. Security admins must deal with numerous entryways through which a malicious actor can gain access or launch a cyber attack.
Each environment in a hybrid cloud has different settings and configurations. This diversity introduces multiple vectors attackers can target. Here are a few vulnerabilities commonly found in hybrid clouds:
- Misconfigured security settings. Malicious actors often target inconsistent security configurations between on-prem and cloud environments.
- Inadequate access controls. Weak or misconfigured access controls allow intruders to gain excessive privileges or access sensitive data.
- Data interception. Data moving between on-prem and cloud components is a prime target for an attack.
- Integration vulnerabilities. Hybrid clouds rely on APIs, gateways, and connectors for communication between different IT environments. Connections between components present opportunities for attackers to exploit flaws and gain unauthorized access or quietly set up a foothold.
- Remote access vulnerabilities. Malicious actors often target users who remotely access hybrid cloud resources.
- Third-party service exploits. Hybrid clouds frequently use third-party databases, analytics tools, and security services. These external dependencies are another common target for attacks.
The interconnected nature of hybrid cloud environments also amplifies the potential impact of a security incident (the so-called blast radius).
While closely related, attack surface and vectors are not synonymous terms. Learn the difference between these two vital security concepts in our >attack vector vs. surface article.
Diverse Security Models
Variations in security requirements in a hybrid cloud architecture present a major challenge. A hybrid cloud strategy must account for and unify the following security elements:
- On-site security measures that keep IT equipment in server rooms safe.
- Measures for protecting private cloud environments (whether hosted on-prem or at a third-party provider).
- Security controls for protecting workloads and data residing in the public cloud.
Each environment in a hybrid cloud requires unique security controls, policies, mechanisms, and practices. Admins must secure components individually and integrate security models to create a safe hybrid environment.
For example, on-prem systems may rely on the traditional LDAP or a domain controller, while public clouds often use cloud-specific IAM solutions. Coordinating and ensuring consistency across these different mechanisms is vital for security.
Visibility Challenges
Monitoring in a hybrid cloud environment is often challenging due to the complex and dynamic nature of the infrastructure. Visibility challenges impact the ability to detect and respond to incidents promptly.
Several factors contribute to the difficulty of effective monitoring in a hybrid cloud, including:
- The mix of multiple interluded yet separate IT environments.
- Inclusions of varying service models, often from different vendors.
- Shared data flows and processes that span multiple systems.
- Complex networking configurations that involve VPNs, cloud on-ramps, and advanced routing.
All major cloud providers offer native monitoring, but integrating these tools with on-prem solutions is complex. Achieving a unified and holistic view of the entire infrastructure is a typical hybrid cloud security challenge.
Check out pNAP's >hybrid cloud solutions and see how we help companies deal with the challenges of hybrid cloud adoption.
Hybrid Cloud Security Best Practices
Securing a hybrid cloud involves a combination of different precautions, policies, and technologies. Below are 10 best practices for ensuring high levels of hybrid cloud security.
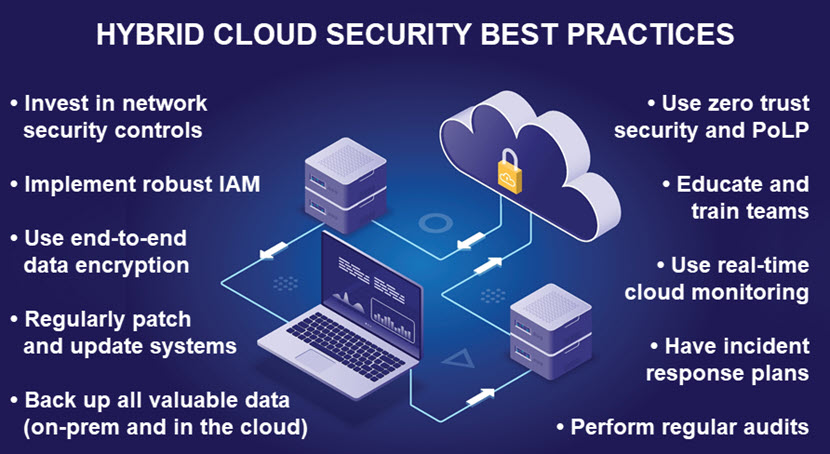
Invest in Network Security Controls
Network security controls are crucial for protecting data in a hybrid cloud. These precautions protect communication channels, prevent unauthorized access, and detect potential threats.
Here's what you can use to improve network security in a hybrid cloud setup:
- Firewalls. Use firewalls to monitor and control incoming and outgoing network traffic. Set up firewalls at various points in the hybrid infrastructure, including between on-prem and cloud environments, within cloud networks, and at the network's edge.
- Intrusion Detection and Prevention Systems (IDPS). IDPSes detect and respond to suspicious activities and potential security threats. These systems analyze network traffic for patterns indicative of malicious behavior and take automated action to mitigate threats.
- Virtual Private Networks (VPNs). Use VPNs to establish secure connections over public networks. They are essential for securing communication between on-prem and public cloud environments.
- Network ACLs. Use network Access Control Lists to control inbound and outbound traffic within cloud environments. Lists help enforce network security rules at the virtual network level.
As an extra precaution, consider segmenting your network to limit the lateral movement of threats. Segmentation helps contain and isolate incidents, reducing the impact of breaches and enhancing overall network security. Boosting endpoint protection is another impactful way to improve network safety.
Implement a Robust IAM Strategy
An Identity and Access Management (IAM) strategy is vital for hybrid cloud security. IAM involves managing and controlling access to resources, systems, and data based on user identities and assigned roles.
Hybrid cloud adopters require a unified approach to identity and access management across the hybrid environment. Most cloud service providers offer native IAM solutions that integrate with on-prem systems. This process typically involves unifying on-prem directories with cloud-based identity services.
Once you create a centralized identity management system, set up the following features and precautions:
- Single Sign-On (SSO). SSO allows users to access multiple apps and services with a single set of credentials. SSO reduces the risk associated with employees managing multiple passwords.
- Role-Based Access Controls (RBACs). Adopt RBAC to assign permissions to users based on their roles within the organization.
- Multi-Factor Authentication (MFA). Require users to provide multiple forms of identification before gaining access to resources.
- Privileged Access Management (PAM). Use PAM to control access to and the use of accounts with elevated permissions.
Use dynamic access policies that adapt based on contextual factors (e.g., user location, device type, or time of access). Dynamic policies add an extra layer of protection by tailoring access controls to specific conditions.
Consider integrating IAM logs with SIEM tools to correlate and analyze security events across the hybrid environment. SIEM tools detect patterns indicative of threats and are a must-have for most cloud security strategies.
Use Encryption Throughout the Data Lifecycle
Encrypting data throughout its lifecycle is a fundamental practice in hybrid cloud security. Encryption safeguards sensitive info from unauthorized access and lowers the threat of data leaks.
Use at-rest encryption to protect data hosted on on-prem servers. You should also encrypt your cloud storage with cloud-native encryption mechanisms provided by the cloud service provider (either through server-side encryption (SSE) or client-side encryption).
In-transit encryption is vital to keep traffic moving throughout your hybrid cloud safe. Use this type of encryption to protect the following data flows:
- On-prem network traffic. Encrypt communication channels between systems within your local on-site infrastructure.
- Inter-cloud communication. Encrypt all data that moves between different cloud environments.
- Hybrid cloud communication. Secure communication between on-prem and cloud environments using encrypted channels.
Consider also using encryption in use to enable systems to process data without the need for decryption during computation. This precaution provides an extra layer of security for sensitive computations.
All three encryption strategies require careful key management to be effective. Follow key management best practices to ensure safe operations.
Our all-in-one >EMP enables you to centralize encryption efforts and control all keys from a single pane of glass.
Regularly Patch Systems
Establish a patch management policy that outlines procedures for identifying, testing, and applying patches in both on-prem and cloud environments. Your patch management policy must address challenges specific to patching in a hybrid cloud environment, such as:
- Coordinating updates across multiple unified platforms.
- Dealing with diverse operating systems and toolsets.
- Managing dependencies between on-prem and cloud-based components.
Regular updates and patches address known vulnerabilities, minimizing the risk of exploits by cyber criminals. Careful patch management also reduces the risk of disparities between on-prem and cloud components, mitigating potential security gaps.
Consider using automated patch management tools that seamlessly integrate with both on-prem and cloud platforms. Automation streamlines the deployment of updates and reduces the time it takes to address vulnerabilities.
Back Up On-Prem and Cloud-Based Data
Data loss can occur for various reasons, including accidental deletion, hardware failures, software glitches, or malicious activity. Data backups provide a safety net, allowing an organization to recover lost or corrupted data in the event of issues with the original files.
Here's what you must do to effectively implement a data backup strategy in a hybrid cloud setting:
- Regularly schedule automated backups of both on-prem and cloud-based critical data.
- Store backups in geographically diverse locations.
- Use immutable backups to prevent ransomware injections.
- Encrypt backups to protect sensitive info.
- Regularly test the restoration process to ensure backup viability.
- Periodically review and update backup policies based on evolving business needs and security risks.
Data backups also reduce the risk of hybrid cloud service outages or disruptions caused by missing data. Backups provide an alternative source of critical info if something happens to the original data set.
Check out pNAP's >backup and restore solutions to see how we ensure our clients never experience permanent data losses.
Implement Zero Trust and PoLP
Zero Trust security and the principle of least privilege (PoLP) are vital to hybrid cloud environments. These strategies minimize the attack surface, limit the impact of incidents, and enhance overall security posture.
The Zero Trust security model is based on the "never trust, always verify" principle. A Zero Trust environment requires verification from everyone, whether inside or outside the network. Here are the key elements of zero trust security:
- Users must provide credentials (2FA of MFA) whenever they log in to their accounts.
- The system must continuously authenticate users and devices based on multiple factors (user behavior, device health, context, etc.).
- Security admins must use granular micro-segmentation to isolate workloads and data.
- Architects must apply security controls at the app layer.
- Systems must analyze patterns and behaviors to detect signs of potential security threats or unauthorized activity.
- The environment must assess compliance with security policies and the presence of up-to-date security software for all devices attempting to access resources.
PoLP is a natural fit for any Zero Trust strategy. PoLP grants users and systems the minimum level of access required to perform their specific tasks. This precaution limits the potential damage an intruder can do with a compromised account or device.

Educate and Train Employees
Provide employees with a contextual understanding of the hybrid cloud model, emphasizing the shared responsibility for security. Organize regular security awareness training that covers the following areas:
- Specific security risks associated with a hybrid environment.
- Guidelines on how employees navigate security risks when using the cloud.
- Instructions on how team members can recognize and report indicators of security incidents, such as signs of phishing, traffic hijacking, or ransomware delivery.
- Guidelines on how regulatory compliance requirements apply to data stored or processed in the hybrid cloud.
Tailor training programs based on employees' roles and responsibilities. Different teams have unique security considerations, so targeted training addresses specific needs. Also, consider running regular simulation exercises to check how prepared employees are to identify and thwart incidents.
Set Up Real-Time Monitoring
The goal of monitoring in hybrid cloud security is to provide an organization with real-time visibility into its security posture. Monitor user activities, network traffic, and system logs to detect security incidents in a timely manner.
Continuous monitoring enables organizations to detect:
- Various anomalies indicative of potential risks.
- Security breaches.
- Unauthorized access attempts.
- Signs of irregular cloud resource usage.
- Opportunities to lower cloud computing costs.
- Shadow IT usage (either on-prem or in the cloud).
- Breaches of compliance measures.
- Unwanted changes in configurations.
- Missing patches and updates.
Monitoring activities must encompass the entire hybrid landscape, including data movement between on-site servers and the cloud. Set up robust logging mechanisms and real-time log analysis to promptly identify any irregularities.
Our article on >cloud monitoring tools presents 30 solutions that help ensure visibility across your cloud environments.
Establish Incident Response Plans
Incident response plans ensure a coordinated and swift reaction to security threats in times of crisis. Outline the most likely and impactful incidents that could occur within your hybrid cloud and prepare how teams should deal with these events.
Most hybrid cloud adopters prepare incident response plans for the following scenarios:
- An intruder gaining unauthorized access.
- Breaches of data moving between on-prem and cloud systems.
- Data exfiltration attempts.
- Malware infections.
- Insider threats.
- Disruptions in communication protocols.
- Unforeseen local incidents (e.g., a power blackout or natural disaster).
- Configuration errors that could lead to exposure.
- A prolonged cloud outage.
Be as detailed as possible in your incident response plans. Set KPIs, calculate optimal RTOs and RPOs, outline clear priorities, and define go-to personnel.
Another good practice is to invest in disaster recovery, either by preparing a DR plan in-house or going with DRaaS. Sound DR ensures you experience little to no downtime once you deal with whatever went wrong within your hybrid cloud.
Our >disaster recovery checklist explains how to create an effective DR plan, plus provides a handy questionnaire to ensure you do not miss anything vital during planning.
Perform Regular Security Assessments
Run vulnerability assessments to identify potential weaknesses in configurations, software, and access controls across the hybrid cloud infrastructure. Perform these audits regularly, and also whenever the team makes any significant tech or infrastructure updates.
Insights gained from vulnerability assessments inform an organization about potential risks, areas for improvement, and adherence to security policies. If relevant to your business, also conduct compliance audits to verify that security measures align with industry regulations.
Another worthwhile way to check your hybrid cloud security is to run periodic penetration tests. These realistic simulations of real-world attacks assess the following areas:
- Overall resilience and efficacy of security measures.
- The teams' readiness to deal with threats.
- The effectiveness of employee training programs and incident response procedures.
If running tests in-house is not an option, engage third-party security experts for independent testing. External assessments provide an unbiased, fresh-eyed perspective and bring seasoned specialists to the evaluation process.
Once you make a plan on how to adopt the best practices discussed above, outline all strategies in a >cloud security policy. A policy standardizes procedures, minimizes security gaps, and ensures a cohesive defense strategy.
Take Zero Chances with Hybrid Cloud Security
The hybrid cloud enables you to leverage the advantages of both on-site and cloud-based systems, but the model comes with a few must-know security challenges. Understanding data flow, access controls, and integration points can help mitigate these risks.
Use what you learned in this article to ensure your organization uses a hybrid cloud without any needless risks to security. Applying best practices also strengthens overall security posture and reduces the likelihood of breaches.