As IT strategies continue to evolve, many organizations are reexamining their relationship with the public cloud. During these reassessments, some companies pull assets off the public cloud and move them to on-prem servers or private clouds.
This process of cloud repatriation (also known as reverse migration or unclouding) is radical and costly, yet an increasing number of companies see this as a worthwhile move. As more businesses consider such a shift, it's vital to understand what's driving this growing trend.
This article outlines the most common reasons why companies are leaving cloud environments in favor of on-site infrastructure. Jump in to learn what's causing this significant shift towards in-house IT and see whether your business would benefit from repatriating cloud workloads.

While some companies pull everything from the public cloud, many decide to only move cloud-based data back to on-prem systems. Check out our article on data repatriation to learn why this practice is gaining so much momentum.
Why Are Companies Leaving the Cloud?
A recent study by Citrix revealed that around 42% of organizations are either considering or have already moved at least half of their public cloud workloads back to on-prem infrastructure. This research surveyed 1,200 businesses in the UK, US, France, and Germany with a revenue exceeding $500 million.
The same report also shows that 93% of surveyed businesses organized at least one cloud repatriation project in the past three years. Let's examine the most common reasons organizations decide to part ways with the public cloud and see what drives such a high number of repatriations.
Want to cut ties with the public cloud without losing all the flexibility of these platforms? Our Bare Metal Cloud enables you to run workloads on dedicated bare metal hardware that you manage with cloud-like agility and simplicity.
High Ongoing Costs
The allure of little to no upfront expenses often masks the ongoing costs of cloud services. Here are the most common cost-related issues companies face when using a public cloud:
- Unpredictable costs. Most cloud providers charge clients based on resource consumption (compute, storage, bandwidth). This pay-as-you-go model often results in unpredictable and escalating costs, especially for businesses with fluctuating workloads.
- Data egress fees. Transferring data out of public cloud environments often incurs significant egress fees, especially for businesses dealing with large volumes of data.
- Hidden costs. Many public cloud providers have hidden expenses, such as fees for API requests or varying storage tiers. Businesses often find it difficult to predict these costs.
- Underutilized resources. Teams often over-provision resources to avoid performance issues. This strategy results in many companies paying for cloud resources they do not fully utilize.
- Expensive extra features. Public cloud providers often bundle additional features or services (advanced analytics, automation, monitoring, etc.) that are unnecessary for many applications.
For some companies, issues with cloud computing costs are enough to warrant a total or partial cloud repatriation. Moving assets back on-prem enables businesses to right-size their infrastructure and ensure they only pay for the capacity they need. Repatriation also eliminates surprise fees associated with sudden usage spikes, data transfers, and unnecessary third-party services.
Repatriation to on-prem servers enables businesses to return to a CapEx model in which they own all the hardware. Over time, this strategy leads to significant IT cost reductions, especially for workloads that don't require the scalability of the public cloud.
Are the high costs the only issue you have with the public cloud? If yes, this problem does not have to be a dealbreaker. Check out these 14 cloud cost management tools that help avoid out-of-hand cloud costs.
Performance and Latency Issues
Public cloud infrastructure can suffer from latency problems or performance bottlenecks. These issues are enough to force some companies into repatriation.
Public cloud environments operate on shared infrastructure in which multiple customers share resources. This multi-tenant model can lead to performance issues during peak demand times. Here are the two most common causes of such problems:
- The noisy neighbor effect. Workloads from one or more tenants in a public cloud can consume an excessive amount of resources (like CPU, memory, or network bandwidth). Some tenants being overly resource-demanding can negatively impact the performance of other users.
- Resource contention. Multiple users competing for the same compute, storage, and network resources can cause reduced system performance. This issue occurs without one specific "noisy" tenant. Instead, performance drops happen because there's insufficient capacity to handle the aggregate demand.
Additionally, cloud providers' data centers are often too far from end users or operations. This issue can introduce latency as data travels long distances, especially if the provider lacks edge servers.
Repatriating to on-prem environments allows companies to set up and use dedicated servers. The lack of other tenants ensures consistent performance. Moving workloads to on-prem data centers also reduces latency by processing data closer to its source.
Moving assets back to private infrastructure eliminates the variability and delays inherent in public cloud environments. However, many businesses also solve performance issues associated with the public cloud with a hybrid cloud strategy that combines on-site and cloud resources.
Cyber Security Concerns
Cyber security risks are a common reason for repatriation as companies increasingly question whether public clouds offer sufficient protection for sensitive data and workloads.
Here are the most common causes of concern surrounding public cloud security:
- Multi-tenancy risks. Public clouds enable multiple clients to utilize the same physical hardware. Multi-tenancy introduces risks, such as data leakage between users or faulty access controls.
- Limited control over data. In the public cloud, providers handle infrastructure security. Limited visibility and control over security measures prevent companies from fully understanding how the provider stores, processes, and protects assets.
- Third-party threats. Public clouds are a popular target for cyber attacks due to the high concentration of data from multiple clients.
- Hands-off responses to incidents. When security incidents occur in a public cloud, the provider's team responds to the threat. Clients cannot control how quickly the security team responds to the danger.
Cloud repatriation significantly improves security if the company has the necessary resources and know-how to keep assets safe on-prem. Here's why many organizations deem repatriation to be beneficial from a security standpoint:
- Moving workloads back on-prem eliminates the risks associated with shared environments.
- On-prem environments allow companies to implement custom security measures. Teams get a chance to ensure optimal protection against the most likely attack vectors.
- Security teams can monitor on-site systems in real-time and respond immediately to potential threats.
Check out our article on cloud security risks to better understand all the potential dangers of using cloud-based resources. You can also read our article on cloud storage security to see to what lengths providers go to keep hosted assets safe from threats.
Vendor Lock-In Concerns
Vendor lock-in is a growing concern for companies relying on public cloud providers. Once an organization deeply integrates its systems with a specific cloud platform, making any radical changes to the infrastructure (i.e., integrating with or switching to another provider) becomes difficult and expensive.
Here's why vendor lock-in is a common consequence of relying on public clouds:
- Proprietary tools and services. Public cloud providers offer specialized tools, APIs, and services unique to their platform. While these services can be convenient, they often make it difficult to transition workloads to another provider without significant reengineering.
- Complex data migrations. Moving large data sets out of a cloud provider's infrastructure is costly due to data egress fees. This process is also technically challenging due to compatibility issues between different platforms.
- Long-term contracts. Many cloud providers offer discounted rates in exchange for long-term commitments. Once a company is locked into a multi-year contract, moving workloads elsewhere results in hefty penalties.
- Data ownership concerns. Businesses often worry about losing full ownership or control of their data when relying on proprietary cloud platforms. Providers may store files in formats that are not easily portable, which further locks businesses into their ecosystem.
The potential lack of flexibility drives many businesses to pursue cloud repatriation in pursuit of greater control over their IT. Repatriation allows companies to move away from proprietary cloud services and adopt more flexible open-source or vendor-neutral solutions, which are easier to alter and migrate.
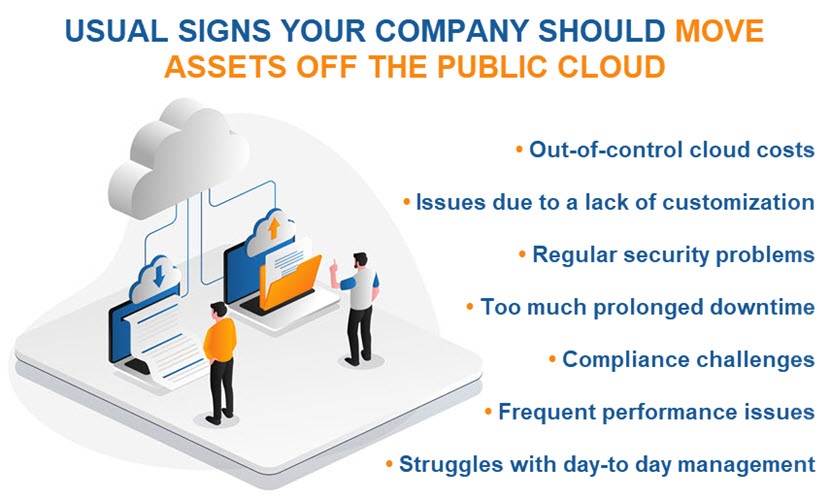
Downtime Concerns
While providers offer high uptime percentages, cloud outages and service disruptions still occur fairly regularly. Even with high uptime guarantees, the cumulative downtime can be a dealbreaker for companies with high availability needs.
Businesses that run mission-critical workloads in the cloud often find interruptions unacceptable. Here are the most common concerns these companies have when using a public cloud:
- Outages. Public cloud providers occasionally experience outages that disrupt business operations and cause downtime. Potential downtime is a major issue for clients who require constant availability.
- Dependency on third-party providers. Clients of public clouds rely entirely on the provider's team for infrastructure maintenance. Any delays in the provider's response to technical problems can cause service interruptions.
- Limited control over failover and recovery. Most providers offer standardized failover solutions that do not fully meet the unique needs of every business. Companies that require faster recovery time objectives (RTOs) or more robust disaster recovery (DR) often find these options lacking.
By moving assets off the public cloud, companies aim to improve system availability and reduce the risks of relying on external providers for uptime and reliability. Companies gain complete control over their infrastructure, which allows them to directly manage system uptime and design custom disaster recovery plans.
Check out pNAP's Disaster-Recovery-as-a-Service (DRaaS) offering to see how we can ensure your critical data and infrastructure remain available in times of crisis.
Data Sovereignty Issues
As businesses expand globally, they must adhere to various data protection laws and regulations. Many of these laws require companies to store and process data within specific geographical regions. Public cloud providers and their globally distributed data centers often make it difficult to ensure compliance with these regulations.
Here are the common data sovereignty concerns with public cloud services:
- Ambiguity of data location. Most public cloud providers operate across multiple regions. Although they offer region-specific hosting options, businesses may struggle to track exactly where providers store and process data. This ambiguity can lead to unintentional non-compliance.
- Cross-border data transfers. Public cloud providers frequently move data between regions for load balancing or redundancy purposes. This practice can violate data sovereignty laws that prohibit transferring data across borders.
- Lack of control over compliance. In shared cloud environments, client companies must solely rely on the provider's adherence to compliance standards.
By repatriating data to on-prem environments, businesses ensure that their data remains within specific jurisdictions and complies fully with relevant data sovereignty laws. On-prem solutions also allow businesses to avoid unnecessary cross-border data transfers, ensuring that sensitive information remains within the legal boundaries of a specific country or region.
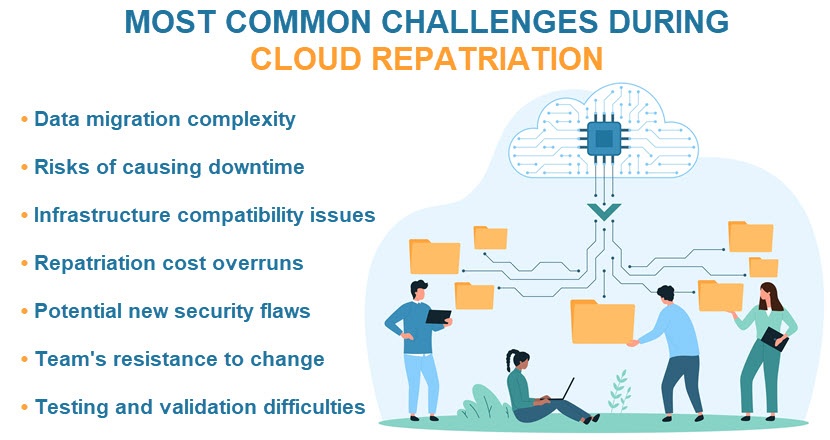
Difficulties in Managing Multi-Clouds
While the initial intent behind a multi-cloud strategy is to avoid vendor lock-in and optimize workloads, the operational challenges of managing multiple clouds often outweigh the benefits. Here's why multi-clouds are so hard to manage:
- Difficult integration. Each public cloud provider operates with different tools and management interfaces. Integrating these platforms into a cohesive system is often tricky.
- Inconsistent security policies. Security measures, data protection standards, and compliance requirements vary widely between cloud providers. Managing security consistently across a multi-cloud environment often introduces vulnerabilities and complicates governance.
- Data fragmentation. Data spread across multiple clouds often becomes fragmented, which makes it challenging to maintain data consistency, security, and accessibility. In some cases, fragmentation can also lead to data corruption.
- Complex performance management. Different clouds offer different performance metrics and monitoring tools. Many teams find it hard to measure and optimize workloads across multiple providers.
Repatriating workloads to a centralized, on-prem infrastructure simplifies management. Companies eliminate the need to coordinate between multiple cloud platforms, making day-to-day operations more streamlined and safer.
Our articles on multi-cloud management and security provide various tips and tricks for keeping your multi-cloud infrastructure cost-effective and safe.
IT Team Skills Gap
Managing and securing a cloud-based infrastructure requires specialized knowledge. Cloud repatriation is a logical move if the in-house team lacks cloud-specific expertise or simply prefers to manage on-prem systems.
Here's where in-house teams most commonly struggle when working with public cloud resources.:
- Complex management tools. Every public cloud service has unique management tools, APIs, and platforms that require specialized knowledge. Many IT teams struggle with the complexity of cloud-based management.
- Security and compliance challenges. Public cloud environments require a deep understanding of cloud-specific security protocols and compliance standards. In-house teams often struggle to implement proper access controls, encryption, and threat monitoring.
- Cost management complexities. Optimizing costs in a cloud environment requires continuous monitoring of usage, scaling resources, and managing reserved instances. Many teams find it difficult to predict and control costs without causing budget overruns.
- Performance optimization. Public cloud platforms offer a range of configuration options for performance, but achieving optimal performance can be complex. Teams often lack the experience to fine-tune instances, storage, and network settings for peak efficiency.
- The rapid evolution of cloud technologies. The public cloud landscape evolves quickly, and providers frequently release new services and features. Keeping up with these changes demands continuous learning, which can overwhelm smaller or less experienced teams.
Cloud repatriation allows certain companies to leverage their existing team's expertise in on-prem infrastructure. Pulling assets back on-prem allows staff members to focus on the technologies they are most familiar with. Companies also reduce the need for ongoing cloud-related training or hiring, which is a major benefit for organizations with limited budgets.

Legacy Application Compatibility Issues
Many businesses discover that, despite initial assessments, their legacy applications or custom-built software do not operate efficiently enough in a public cloud. This issue commonly occurs for several reasons:
- Legacy software. Many companies run critical operations on older, monolithic applications not designed for cloud architecture. These systems often fail to transition smoothly to cloud-based platforms as they are incompatible with modern cloud services.
- Customization challenges. Applications that go through heavy customization to meet specific needs often rely on unique configurations that public clouds may not support effectively. As a result, businesses might encounter unforeseen limitations in cloud infrastructure that prevent these apps from functioning optimally.
- Dependency on on-prem resources. Some apps depend on on-prem resources (specific hardware, databases, proprietary systems, etc.) that are difficult to replicate in the cloud.
- Performance considerations. Legacy applications may require specific performance characteristics (such as low latency or high IOPS) that public cloud offerings cannot provide consistently.
Moving workloads back to on-prem environments is a common fix when companies face these issues. This shift allows businesses to regain the control and flexibility needed to ensure their critical applications run efficiently and reliably.
Lack of Hardware Control
Another common reason companies are leaving cloud environments is the need for complete control over computing power, storage, and the network. Many businesses find that the lack of direct control over cloud resources creates limitations, particularly in terms of performance tuning and custom infrastructure needs.
Repatriating workloads to on-prem infrastructure allows companies to tailor resources according to their exact needs. This move ensures maximum efficiency without the constraints imposed by a third-party provider. Meanwhile, companies also get to enjoy other benefits of total infrastructure control, such as:
- The ability to directly control how resources are allocated across applications and workloads.
- A clearer and more transparent understanding of infrastructure costs.
- The ability to respond more quickly to changing resource needs without having to wait for a cloud provider's approval or experiencing delays in resource scaling.
- Improved reliability and uptime as businesses can proactively address issues without relying on third-party providers.
Planning to set up an on-site server room for your recently repatriated workloads? Our article on server room designs helps make the right decisions during this process.
Do Not Be Afraid to Repatriate Public Cloud Assets
At first glance, repatriating assets appears to be equivalent to admitting a mistake. However, there was a reason why you placed these assets in the cloud in the first place, and you now have a valid reason why those workloads require repatriation. Do not hesitate to move workloads and data off the public cloud if it's clear that your business would benefit from such a move.