Anonymous proxies facilitate the concealment of the user's IP address and, by extension, their identity and geographic location. These proxies are used for various purposes, including enhancing online privacy, circumventing access restrictions, and protecting the confidentiality of internet communications.
What Is Anonymous Proxy?
An anonymous proxy server is a network intermediary that acts as a gateway between a client and the target server. It intercepts the client's outbound requests, processes them, and forwards them to the destination server while substituting the client's IP address with its own. This IP substitution effectively anonymizes the client by concealing their true network identity from the destination server and any potential interceptors.
Anonymous proxies are typically implemented to enhance user privacy, bypass geo-blocks, and mitigate third-party tracking.
How Does an Anonymous Proxy Server Work?
Here is how an anonymous proxy maintains client anonymity:
- Client configuration and proxy engagement. The client system is configured to route its traffic through the proxy server by setting the proxy's IP address and port in the network or browser settings. This configuration establishes the proxy as the primary handler of all outgoing requests.
- Request interception and header processing. When the client initiates a connection to a web service, the request is intercepted by the anonymous proxy server. The proxy server examines the request headers and removes or alters fields that could reveal the client's IP address or other identifying information, such as the HTTP X-Forwarded-For header.
- Anonymization process. The proxy then substitutes the client's IP address with its own within the modified request headers. If the proxy server is an elite proxy, it will also obscure any evidence that the request is being proxied, making it indistinguishable from a direct request by the proxy itself.
- Forwarding and response handling. The anonymized request is forwarded to the target server, which processes it and sends the response back to the proxy server. The proxy then relays the server's response back to the client. The client's IP address remains concealed from the target server throughout this exchange.
- Logging and privacy considerations. Request logs may be maintained depending on the proxy server's configuration and policies. High-anonymity proxies typically minimize or eliminate logging to enhance privacy. The security of the proxy server itself, including its susceptibility to traffic analysis or interception, also plays a crucial role in the overall effectiveness of anonymization.
Anonymous Proxy Uses
Anonymous proxies are used across various domains where preserving anonymity and bypassing restrictions are vital. Their applications include:
- Privacy and data protection. Users leverage anonymous proxies to obfuscate their IP addresses during web browsing, preventing tracking and data collection by advertisers, websites, and other entities. This process ensures that personal data remains private and reduces the risk of profiling.
- Geo-restriction and censorship circumvention. By routing traffic through proxies located in different regions, users can bypass geographic restrictions and access content that may be blocked or censored in their country. This capability is particularly useful in regions with strict internet censorship laws.
- Security enhancements in adverse environments. In environments where internet traffic is monitored or controlled by malicious actors, anonymous proxies provide a layer of protection by masking the user's identity and making it harder for attackers to target them.
- Mitigating IP-based rate limiting and bans. Users can avoid IP-based restrictions, such as rate limiting or bans imposed by certain websites or services, by rotating through different proxy servers, each presenting a unique IP address to the target server.
Anonymous Proxy Types
Anonymous proxies are categorized based on their anonymity features and the level of information they expose to the destination server. The primary types include:
- Transparent proxies. Transparent proxies do not conceal the client's IP address; instead, they forward the original IP address to the target server along with the request. These proxies are primarily used for content filtering and caching but do not offer anonymity. The target server knows the request is being proxied and knows the client's IP address.
- Anonymous proxies. Anonymous proxies mask the client's IP address by replacing it with the proxy server's IP address in the forwarded request. However, they still reveal that a proxy is used through identifiable headers or protocol behaviors. These proxies provide moderate anonymity by preventing direct exposure of the client's IP address.
- Elite proxies (high anonymity proxies). Elite proxies offer the highest degree of anonymity by concealing the client's IP address and removing or modifying any headers that might indicate the use of a proxy. As a result, the target server cannot distinguish whether the request is proxied or direct, ensuring maximum anonymity.
Protocol-specific Anonymizers
Protocol-specific anonymizers are specialized tools designed to provide anonymity for specific types of network traffic or applications. These anonymizers optimize anonymity within the context of the protocols they support:
- HTTP proxies. HTTP proxies are designed to handle HTTP traffic exclusively. They forward HTTP requests from the client to the web server, altering headers to anonymize the client. These proxies are commonly used for web browsing but are limited to the HTTP and HTTPS protocols, lacking the capability to handle other types of traffic such as FTP or P2P.
- SOCKS proxies. SOCKS proxies function at the session layer, providing a more versatile solution than HTTP proxies by supporting various types of traffic, including TCP and UDP. SOCKS5, the latest version, includes advanced features such as authentication and support for IPv6, making it suitable for a wide range of applications beyond web browsing, including email, file transfers, and streaming.
- VPNs (virtual private networks). VPNs operate at a lower level than traditional proxies by establishing a secure, encrypted tunnel between the client and the VPN server. While VPNs can anonymize all types of traffic by routing it through the VPN server, they are not strictly categorized as proxies. VPNs offer comprehensive anonymity and are often used to secure all internet communications from a device.
Protocol-independent Anonymizers
Protocol-independent anonymizers anonymize any type of internet traffic, regardless of the protocol. These tools are applicable in a broad range of scenarios and offer flexibility across different network applications:
- Tor (The Onion Router). Tor is a decentralized, volunteer-operated network that anonymizes internet traffic by routing it through multiple nodes, each adding a layer of encryption. This process, known as onion routing, significantly complicates traffic analysis and makes it difficult to trace the origin of the communication. Tor supports various applications, including web browsing, messaging, and file sharing, and is known for providing strong anonymity at the cost of performance.
- I2P (Invisible Internet Project). I2P is an anonymizing network layer that facilitates anonymous peer-to-peer communication. Unlike Tor, which is primarily used for accessing the public internet, I2P is designed to create and access services within its own network, known as the "I2P network." It supports secure and anonymous hosting of websites, messaging, and file sharing, providing end-to-end encryption and traffic obfuscation.
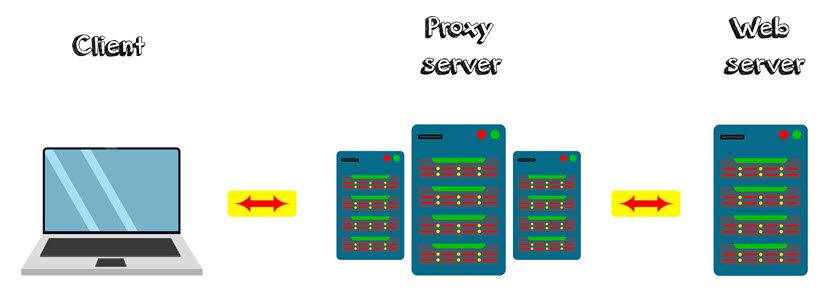
Anonymous Proxies Advantages and Disadvantages
Using anonymous proxies is a trade-off between privacy, performance, and security.
Advantages
Here are the benefits of anonymous proxies:
- IP address obfuscation. Anonymous proxies conceal the client's IP address, protecting their identity from being directly exposed to websites, advertisers, and other tracking entities. This added protection reduces the risk of personal data leakage and targeted attacks.
- Bypassing geographic and content restrictions. By connecting to proxy servers in different locations, users can circumvent regional blocks and censorship, accessing content that may otherwise be inaccessible due to geographic restrictions or governmental controls.
- Security against surveillance. In environments with high levels of monitoring or censorship, anonymous proxies provide a layer of security by preventing direct tracing of the client's internet activity, thus mitigating the risk of targeted surveillance or legal repercussions.
- Dynamic IP management. By employing multiple proxy servers with different IP addresses, users can rotate their apparent IP location, avoiding IP-based rate limiting, bans, and other restrictions online services impose.
Disadvantages
Here are the drawbacks of anonymous proxies:
- Increased latency and performance overhead. The additional network hops introduced by routing traffic through a proxy server lead to increased latency and reduced throughput, particularly when using geographically distant proxies or handling large traffic volumes.
- Security vulnerabilities. While anonymous proxies offer IP address concealment, they may not provide robust encryption or protection against sophisticated threats. The proxy server's security is a critical concern, as compromised or malicious proxies can lead to data interception or misuse.
- Trust and reliability issues. Users must trust that the proxy server operator will not log or misuse their data. This reliance on the proxy operator's integrity is a potential weak point, especially if an unknown or untrusted entity manages the proxy. Additionally, the reliability and uptime of the proxy service can affect its usability for critical applications.
How to Choose an Anonymous Proxy Service?
Choosing the right anonymous proxy service involves evaluating the following factors:
- Anonymity and security levels. Determine the level of anonymity required based on the intended use. Elite proxies or services offering high anonymity are essential for activities demanding maximum privacy. Evaluate the service's security measures, including encryption, logging policies, and protection against common threats like DNS leaks.
- Network performance and latency. Assess the proxy service's network performance, focusing on metrics such as latency, bandwidth availability, and server uptime. High-performance proxies are crucial for applications where low latency and high-speed data transmission are required.
- Server distribution and availability. Examine the geographic distribution of the proxy servers. A well-distributed network of servers across multiple regions enhances flexibility and access to geographically restricted content.
- Reputation and provider trustworthiness. Research the proxy provider's reputation, including user reviews, historical security incidents, and transparency regarding data handling practices. Trustworthy providers are more likely to maintain high service quality and respect user privacy.
- Cost and subscription flexibility. Compare the pricing structures of different services, considering the balance between cost and the level of anonymity, performance, and support provided. Free proxy services may offer limited features or bandwidth, while paid services typically provide better performance, security, and customer support.