In the dynamic world of cybersecurity, there is a constant influx of new solutions promising to address every concern. Extended Detection and Response (XDR) is the new player in this space, catching the attention of many organizations seeking enhanced protection. But does it deliver on its promises, and is it worth the investment?
This article explores the capabilities of XDR and compares it to other detection and response technologies.
What Is XDR?
An XDR system is a cybersecurity platform that integrates multiple security tools to detect and respond to cyber attacks. XDR collects data and feeds it into an analytics engine that identifies and prioritizes potential security threats. If it detects one, it automatically or manually isolates the threat, blocks access, and removes malware.
The main selling point of XDR is that it is highly modular and flexible. It integrates multiple security tools to provide a unified view of an organization's IT infrastructure. These integrations also enable the sharing of threat intelligence and the coordination of automated responses within the XDR framework.
There are two main types of XDR systems, categorized based on their deployment models and integration approaches:
- Native XDR. This type of extended detection and response is provided by a single vendor and integrates fully with the vendor’s ecosystem. As an all-in-one platform, this solution provides a unified interface and consistent user experience. However, integrations with third-party security solutions can be limited.
- Open or hybrid XDR. This type of XDR is vendor-agnostic and allows easy integration with an array of third-party security tools. It connects existing security tools and provides a central management platform. This model is more flexible but requires extensive configuration and management.
Why Do Businesses Need XDR?
XDR addresses many cybersecurity challenges:
- Security tools sprawl. XDR consolidates multiple security tools into a single platform, eliminating the need for individual solutions.
- Alert fatigue. By integrating data from various sources and applying advanced analytics, XDR prioritizes and filters alerts, reducing the volume of false positives.
- Operational costs. An XDR system’s automation capabilities streamline incident response, reducing the time and resources needed to address security breaches.
- Lack of visibility. XDR provides a full view of the security landscape across different layers of an organization’s infrastructure, facilitating the response to security incidents.
- Complexity. XDR systems reduce complexity by unifying multiple security tools under one platform.
- Training costs. With XDR, personnel only need to learn to use a single platform, reducing the time and cost of training and certifications.
- Maintenance costs. An XDR platform centralizes maintenance, reducing the time and resources required to secure an organization’s IT infrastructure.
How Does XDR Work?
XDR is a new and evolving technology. There are no universal features, and every vendor specializes in certain security aspects. However, all XDR solutions contain the following elements:
Data Collection
XDR systems collect data from sources such as:
- Endpoints, such as laptops, desktops, servers, and mobile devices.
- Networks, including routers, switches, firewalls, and intrusion detection systems.
- Clouds, encompassing infrastructure, applications, and storage.
- Applications, both on-premises and cloud-based.
Data Normalization and Storage
XDR solutions collect data from a wide range of sources that use different formats, terminology, and units of measurement. They transform the data into a coherent format, allowing for meaningful comparison.
Data Correlation and Analysis
XDR solutions identify the patterns that signal an attack. Here are some examples of anomalies that an XDR system might catch:
- Unusual spikes in traffic volume or communication with a suspicious IP address.
- Unexpected file modifications, executions, or data transfers.
- Abnormal login times, access to unauthorized resources, or excessive data downloads that suggest account takeover or an insider threat.
Threat Detection
XDR solutions use three primary methods to detect threats.
- Signature-based detection. Identifies threats by comparing collected data to a database of malware signatures. This technique is highly effective against known threats but may miss emerging or zero-day attacks.
- Anomaly-based detection. Assumes that malicious activity manifests deviations from normal behavior. Anomaly-based detection is useful for identifying threats that may not yet have established signatures.
- Machine learning-based detection. Utilizes algorithms to identify patterns that suggest malicious activity. This approach is more advanced than anomaly-based detection but is complex to implement and maintain.
Threat Investigation and Response
After the XDR system detects a threat, it gives the security team the information they need to respond quickly and effectively. Here are the key detection, mitigation, and analysis functions that XDR performs:
- Identifies the attack vector and the device, network, or application responsible for the data breach.
- Determines the scope of the threat and the potential damage.
- Quarantines compromised systems and devices, blocks malicious activity, and disinfects affected endpoints.
- Facilitates post-incident analysis through detailed logs and reports of the incident timeline, affected systems, and remediation actions.
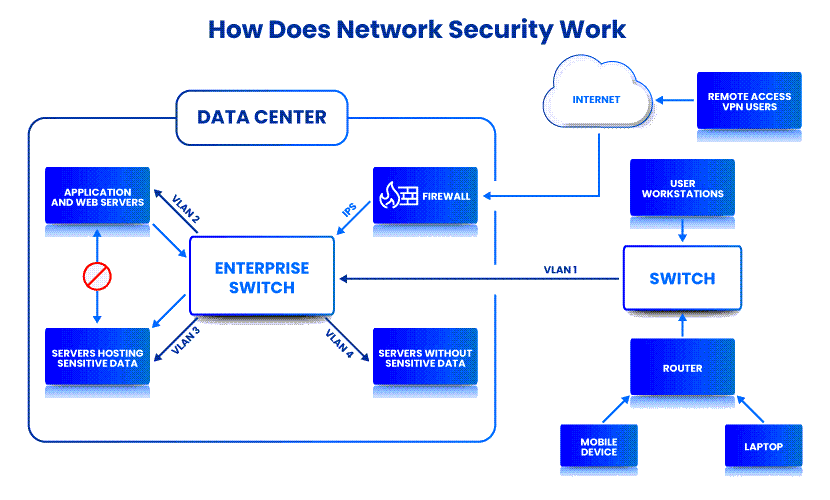
Our article on the types of network security explains the methods companies use to keep their networks safe.
XDR vs. Other Detection & Response Technologies
The security industry's dynamic nature leads to the rapid evolution of terminology and, consequently, to overlap and misunderstanding. To provide clarity on the subject, below is a comparison of XDR with other detection and response technologies:
EDR vs. XDR
Endpoint Detection and Response (EDR) involves blocking and logging code execution on network endpoints, such as laptops, desktops, and mobile phones. EDR focuses exclusively on endpoint security.
On the other hand, XDR is an evolution of EDR, expanding its scope to incorporate network security, protection, and analysis.
XDR vs. SIEM
A security information and event management (SIEM) system is a centralized repository for logs and telemetry data. Security teams use it to create alerts, workflows, dashboards, and other tools for security management.
An XDR system is not meant to be a replacement for SIEM. However, the line between them blurs with a well-implemented XDR. Ideally, each serves a distinct purpose and has its particular strengths and weaknesses. Some XDR solutions even rely on SIEM platforms as their backend.
If you must choose only one, an XDR solution might suffice if your focus is on security posture management, detection, and remediation. On the other hand, an SIEM system is vital if you have compliance requirements for log retention or need comprehensive log analysis.
MDR vs. XDR
Managed detection and response (MDR) is a cybersecurity service that outsources the burden of network monitoring, incident analysis, and response to a team of dedicated experts. MDR providers typically use their own tools to respond to threats 24/7.
On the other hand, XDR can be either a managed service or a self-managed solution. Organizations that lack the resources or expertise to self-manage should consider managed XDR. Conversely, companies that need to retain more control over their systems prefer to self-manage.
We partnered with VMware and Intel to develop Data Security Cloud, a cutting-edge platform that offers unparalleled protection against a wide range of cyberattacks.
Leveraging the latest MDR practices, Data Security Cloud provides a comprehensive suite of features, including advanced data protection, vulnerability scanning, and endpoint protection.
Key Takeaways
While XDR promises to unify your security stack out of the box, the reality can vary depending on the provider and your needs. Make sure that the chosen solution integrates seamlessly with your existing tools and processes without the need for disruptive overhauls or workarounds. Furthermore, if your organization already has a robust security architecture, consider whether the added functionalities of an XDR system outweigh the potential integration challenges.
Finally, be aware that the success of any self-managed security tool hinges on your in-house talent's expertise and the ability to implement and use the technology effectively.